There are different ways of providing integrity and authentication within cryptography. What type of technology is shown in the graphic that follows?

A.
One-way hash
B.
Digital signature
C.
Birthday attack
D.
Collision
Explanation:
B: When a hash algorithm is applied to a message, it produces a message digest, and this value is signed with a private key to produce a digital signature. It provides authentication,
data integrity, and nonrepudiation. The act of signing is the actual encryption of the value with the private key. When Maureen receives the message, she will perform the hashing
function on the message and come up with her own hash value. Then she will decrypt the sent hash value (digital signature) with Kevin’s public key. She then compares the two
values, and if they are the same, she can be sure the message was not altered during transmission. She is also sure the message came from Kevin because the value was encrypted
with his private key.
A is incorrect because a one-way hash is a function that takes a variable-length string and a message and produces a fixed-length value called a hash value. For example, if Kevin
wants to send a message to Maureen and he wants to ensure the message does not get altered in an unauthorized fashion while it is being transmitted, he would calculate a hash
value for the message and append it to the message itself. When Maureen receives the message, she performs the same hashing function Kevin used and then compares her result
with the hash value sent with the message. If the two values are the same, Maureen can be sure the message was not altered during transmission. If the two values are different,
Maureen knows the message was altered, either intentionally or unintentionally, and she discards the message.
C is incorrect because a birthday attack is an attack on hashing functions through brute force. The attacker tries to create two messages with the same hashing value. A good
hashing algorithm should not produce the same hash value for two different messages. If the algorithm does produce the same value for two distinctly different messages, this is called
a collision. An attacker can attempt to force a collision, which is referred to as a birthday attack. Hash algorithms usually use message digest sizes (the value of n) that are large
enough to make collisions difficult to accomplish, but they are still possible. An algorithm that has 160-bit output, like SHA-1, may require approximately 280 computations to break. This
means there is a less than 1 in 280 chance that someone could carry out a successful birthday attack. A hashing algorithm that has a larger bit output is less vulnerable to bruteforce
attacks such as a birthday attack.
D is incorrect because a collision is when two hashed messages result in the same value. A strong one-hash function should not provide the same hash value for two or more
different messages. If a hashing algorithm takes steps to ensure it does not create the same hash value for two or more messages, it is said to be collision free. If a hashing algorithm
generates a message digest of 60 bits, there is a high likelihood that an adversary can find a collision using only 230 inputs.


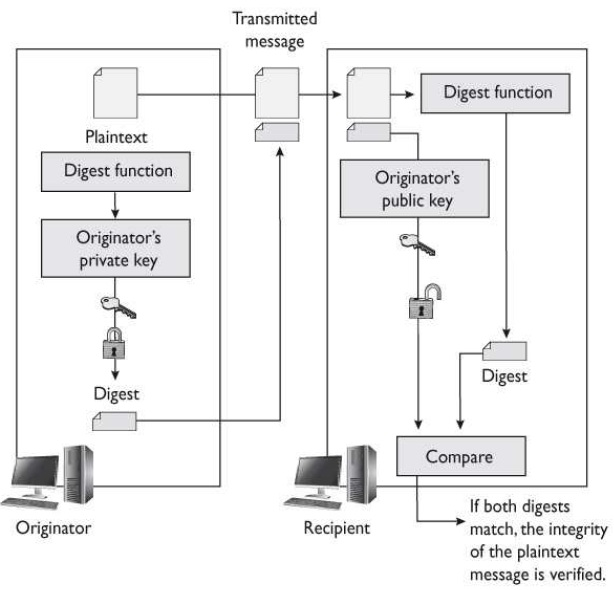
When a hash algorithm is applied to a message, it produces a message digest, and this value is signed with a private key to produce a digital signature.
0
0