There are several types of attacks that programmers need to be aware of. What attack does the graphic that follows illustrate?

A.
Traffic analysis
B.
Race condition
C.
Covert storage
D.
Buffer overflow
Explanation:
D: A buffer is an area reserved by an application to store something in it, like some user input. After the application receives the input, an instruction pointer points the application to
do something with the input that’s been put in the buffer. A buffer overflow occurs when an application erroneously allows an invalid amount of input to be written into the buffer area,
overwriting the instruction pointer in the code that told the program what to do with the input. Once the instruction pointer is overwritten, whatever code has been placed in the buffer
can then be executed, all under the security context of the application.
A is incorrect because traffic analysis is a method of uncovering information by watching traffic patterns on a network. For example, heavy traffic between the HR department and
headquarters could indicate an upcoming layoff. Another example is if there is a lot of traffic between two military units, this may indicate that a military attack is being planned. Traffic
padding can be used to counter this kind of attack, in which decoy traffic is sent out over the network to disguise patterns and make it more difficult to uncover them.
B is incorrect because when two different processes need to carry out their tasks on a resource, they need to follow the correct sequence. Process one needs to carry out its work
before process two accesses the same resource and carries out its tasks. If process two goes before process one, the outcome could be very different. If an attacker could manipulate
the processes so that process two did its thing first, she is controlling the outcome of the processing procedure, which is referred to as a race condition attack.
C is incorrect because in a covert storage channel, processes are able to communicate through some type of storage space on the system. For example, System A is infected with a
Trojan horse that has installed software that will be able to communicate to another process in a nefarious way. System A has a very sensitive file (File 2) that is of great interest to a
particular attacker. The software the Trojan horse installed is able to read this file and it needs to send the contents of the file to the attacker, which can only happen one bit at a time.
The intrusive software is going to communicate to the attacker by locking a specific file (File 3). When the attacker attempts to access File 3 and finds it has a software lock enabled on
it, the attacker interprets this to mean the first bit in the sensitive file is a 1. The second time the attacker attempts to access File 3, it is not locked. The attacker interprets this value to
be zero. This continues until all of the data in the sensitive file are sent to the attacker.


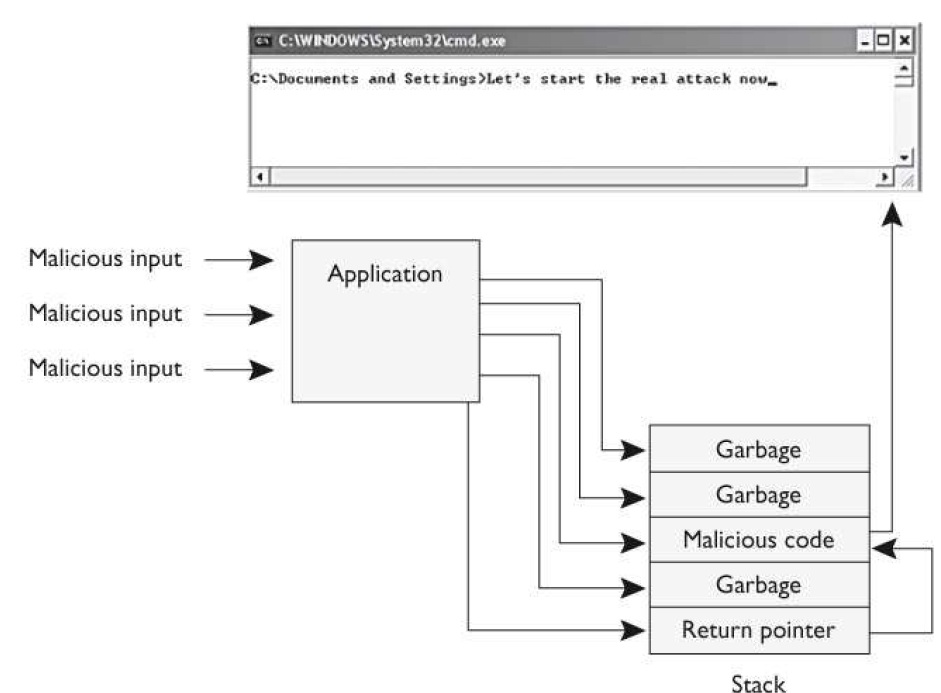
A buffer overflow occurs when an application erroneously allows an invalid amount of input to be written into the buffer area,
overwriting the instruction pointer in the code that told the program what to do with the input.
0
0