Different access control models provide specific types of security measures and functionality in applications and operating systems. What model is being expressed in the graphic that follows?

A.
Noninterference
B.
Biba
C.
Bell-LaPadula
D.
Chinese Wall
Explanation:
D: The Chinese Wall model was created to provide access controls that can change dynamically, depending upon a user’s previous actions. The main goal of the
model is to protect against conflicts of interest by users’ access attempts. For example, if a large marketing company provides marketing promotions and materials for
two banks, an employee working on a project for Bank A should not look at the information the marketing company has on its other bank customer, Bank B: Such action
could create a conflict of interest because the banks are competitors. If the marketing company’s project manager for the Bank A project could view information on Bank
B’s new marketing campaign, he may try to trump its promotion to please his more direct customer.
A is incorrect because multilevel security properties can be expressed in many ways, one being Noninterference. The Chinese Wall model does not focus on
multilevel security properties and the Noninterference model does not focus on conflicts of interest. The concept of noninterference is implemented to ensure any
actions that take place at a higher security level do not affect, or interfere with, actions that take place at a lower level and vice versa. This type of model does not
concern itself with conflicts of interest, but rather with what a subject knows about the state of the system. So if an entity at a higher security level performs an action, it
cannot change the state for the entity at the lower level. The Noninterference model is also focused on confidentiality. It works to ensure that subjects at a lower
clearance level cannot access data or objects at a higher clearance level.
B is incorrect because the Biba is a state machine model that addresses the integrity of data within applications without the use of a wall construct. Although the Biba
model is very similar to the Bell-LaPadula model, the Bell-LaPadula model uses a lattice of security levels (top secret, secret, sensitive, and so on). These security
levels were developed mainly to ensure that sensitive data was only available to authorized individuals. The Biba model is not concerned with security levels and
confidentiality, so it does not base access decisions upon this type of lattice. The Biba model uses a lattice of integrity levels. Biba compartmentalizes data based on
integrity levels. It is an information flow model that controls information flow in a way that is intended to protect the integrity of the most trusted information. The Biba
model was not built to address conflicts of interest.
C is incorrect because a system that employs the Bell-LaPadula model is called a multilevel security system, meaning users with different clearances use the system,
and the system processes data at different classification levels. The level at which data is classified determines the handling procedures that should be used. The Bell-
LaPadula model is a state machine model that enforces the confidentiality aspects of access control. A matrix and security levels are used to determine if subjects can
access different objects. The subject’s clearance is compared to the object’s classification and then specific rules are applied to control how subject-to-object
interactions can take place. The Bell-LaPadula model was not developed to address conflicts of interest.


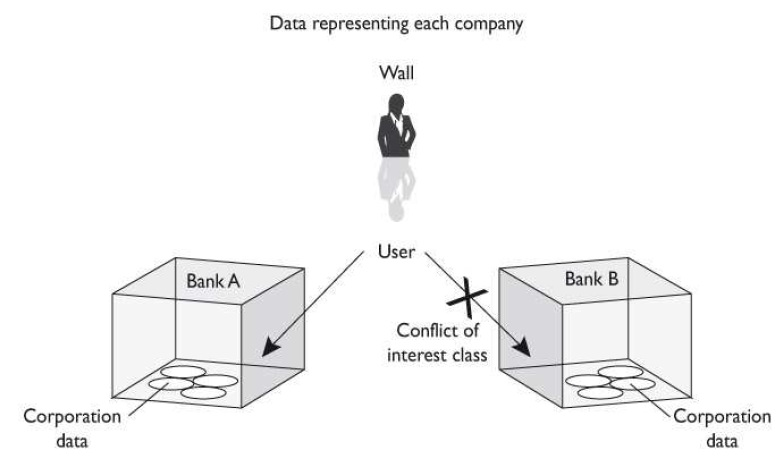
The Chinese Wall model was created to provide access controls that can change dynamically, depending upon a user’s previous actions. The main goal of the
model is to protect against conflicts of interest by users’ access attempts.
中國牆模型的建立是為了提供一個可以動態地變化,這取決於用戶的以前的操作的訪問控制。的主要目標
模型是用戶的訪問企圖,以防止利益衝突
0
0