There are several different types of technologies within cryptography that provide confidentiality. What is represented in the graphic that follows?

A.
Running key cipher
B.
Concealment cipher
C.
Steganography
D.
One-time pad
Explanation:
D: A one-time pad is a perfect encryption scheme because it is considered unbreakable if implemented properly. A one-time pad uses a pad with random values that are XORed
against the message to produce ciphertext. The plaintext message shown in the graphic that needs to be encrypted has been converted into bits, and our one-time pad is made up of
random bits. This encryption process uses a binary mathematical function called exclusive-OR, usually abbreviated as XOR. The receiver must have the same one-time pad to decrypt
the message, by reversing the process.
A is incorrect because a running key cipher uses a key that does not require an electronic algorithm and bit alterations but cleverly uses components in the physical world around
you. For instance, the algorithm could be a set of books agreed upon by the sender and receiver. The key in this type of cipher could be a book page, line number, and column count. If
I get a message from my super-secret spy buddy and the message reads “149l6c7.299l3c7.911l5c8,” this could mean for me to look at the 1st book in our predetermined series of
books, the 49th page, 6th line down the page, and the 7th column. So I write down the letter in that column, which is m. The second set of numbers starts with 2, so I go to the 2nd
book, 99th page, 3rd line down, and then to the 7th column, which is p. The last letter I get from the 9th book, 11th page, 5th line, 8th column, which is t. So now I have come up with
my important secret message, which is mpt.
B is incorrect because a concealment cipher is a message within a message. If my spy buddy and I decide our key value is every third word, then when I get a message from him, I
will pick out every third word and write it down. Suppose he sends me a message that reads, “The saying, ‘The time is right’ is not cow language, so is now a dead subject.” Because
my key is every third word, I come up with “The right cow is dead.”
C is incorrect because steganography is a method of hiding data in another media type so that the very existence of the data is concealed. Only the sender and receiver are
supposed to be able to see the message because it is secretly hidden in a graphic, wave file, document, or other type of media. The message is not encrypted, just hidden. Encrypted
messages can draw attention because it tells the bad guy, “This is something sensitive.” A message hidden in a picture would not attract this type of attention, even though the exact
same secret message can be embedded into this image. Steganography is a type of security through obscurity.


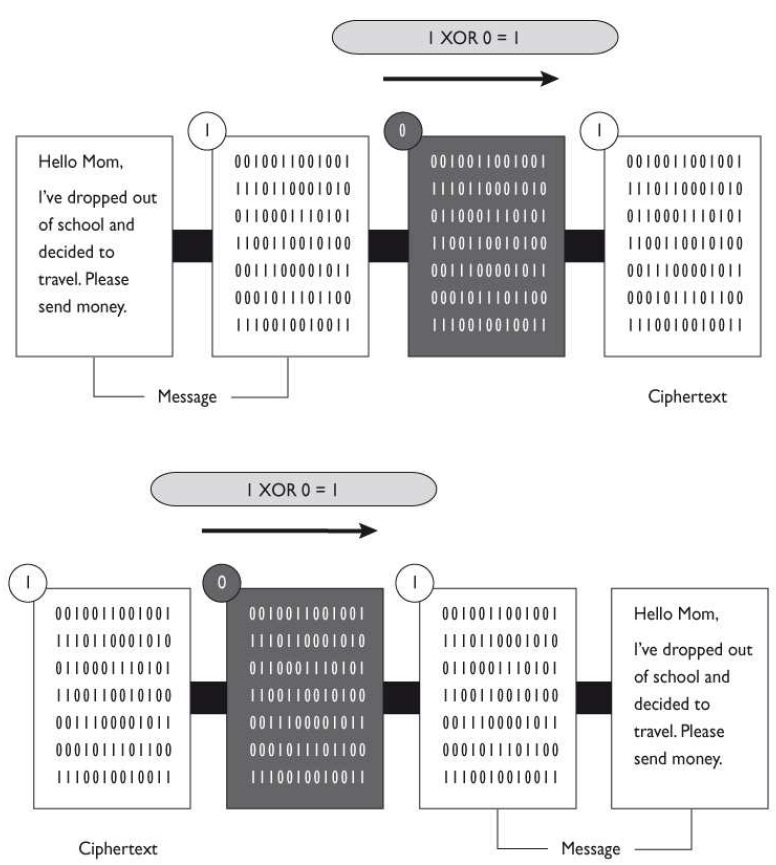
Run Time Pad (XOR): A one-time pad is a perfect encryption scheme because it is considered unbreakable if implemented properly. A one-time pad uses a pad with random values that are XORed against the message to produce ciphertext.
A running key cipher: uses a key that does not require an electronic algorithm and bit alterations but cleverly uses components in the physical world around
you.
A concealment 隱蔽 cipher is a message within a message. If my spy buddy and I decide our key value is every third word, then when I get a message from him, I
will pick out every third word and write it down. Suppose he sends me a message that reads, “The saying, ‘The time is right’ is not cow language, so is now a dead subject.”
0
0