There are several security enforcement components that are commonly built into operating systems. Which component is illustrated in the graphic that follows?

A.
Virtual machines
B.
Interrupt
C.
Cache memory
D.
Protection rings
Explanation:
D: An operating system has several protection mechanisms to ensure processes do not negatively affect each other or the critical components. One security
mechanism commonly used in operating systems is protection rings. These rings provide strict boundaries and definitions for what the processes that work within each
ring can access and what operations they can successfully and securely execute. The processes that operate within the inner rings have more privileges than the
processes operating in the outer rings, because the inner rings only permit the most trusted components and processes to operate within them. Protection rings support
the availability, integrity, and confidentiality requirements of multitasking operating systems. The most commonly used architecture provides four protection rings:Ring0 Operating system kernel
Ring1 Remaining parts of the operating system
Ring2 I/O drivers and utilities
Ring3 Applications and user activityA is incorrect because a virtual instance of an operating system is known as a virtual machine. A virtual machine is commonly referred to as a guest that is executed
in the host environment. Virtualization allows a single host environment to execute multiple guests at once, with multiple virtual machines dynamically pooling resources
from a common physical system. Computer resources such as RAM, processors, and storage are emulated through the host environment. The virtual machines do not
directly access these resources; instead, they communicate with the host environment responsible for managing system resources. Virtual machines do not work in a
circular framework as shown in the graphic.
B is incorrect because an interrupt is a function used in operating systems that allows for slots of the CPU to be used. The most basic CPUs can do only one thing at
a time. So the system has hardware and software interrupts. When a device needs to communicate with the CPU, it has to wait for its interrupt to be called upon. The
same thing happens in software. Each process has an interrupt assigned to it. It is like pulling a number at a customer service department in a store. You can’t go up to
the counter until your number has been called out. When a process is interacting with the CPU and an interrupt takes place (another process has requested access to
the CPU), the current process’s information is stored in the process table, and the next process gets its time to interact with the CPU.
C is incorrect because cache memory is a type of memory used for high-speed writing and reading activities and it is not necessarily a security mechanism. When the
system assumes (through its programmatic logic) that it will need to access specific information many times throughout its processing activities, it will store the
information in cache memory so it is easily and quickly accessible. Data in cache can be accessed much more quickly than data stored in real memory. Therefore, any
information needed by the CPU very quickly, and very often, is usually stored in cache memory, thereby improving the overall speed of the computer system. Cache
memory also does not work in a circular framework as illustrated in the graphic.


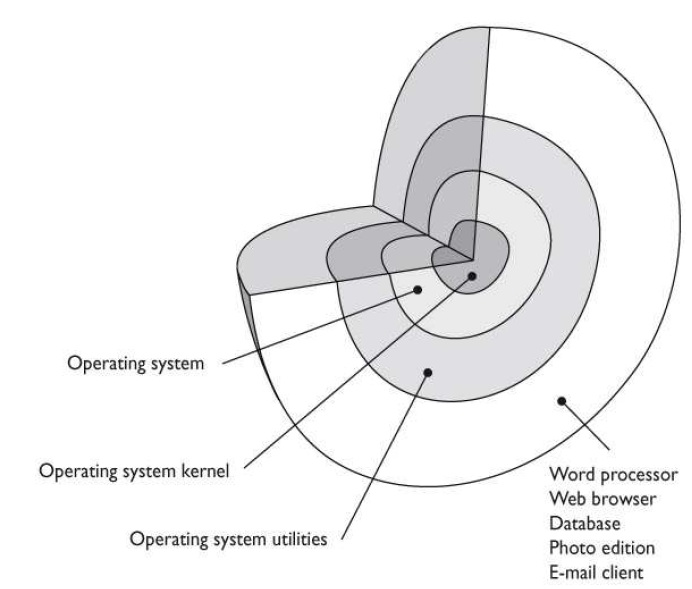
Rings provide strict boundaries and definitions for what the processes that work within each ring can access and what operations they can successfully and securely execute.
環提供嚴格的界限和定義了每個環內工作的進程可以訪問,他們可以成功地和安全地執行什麼操作。
0
0