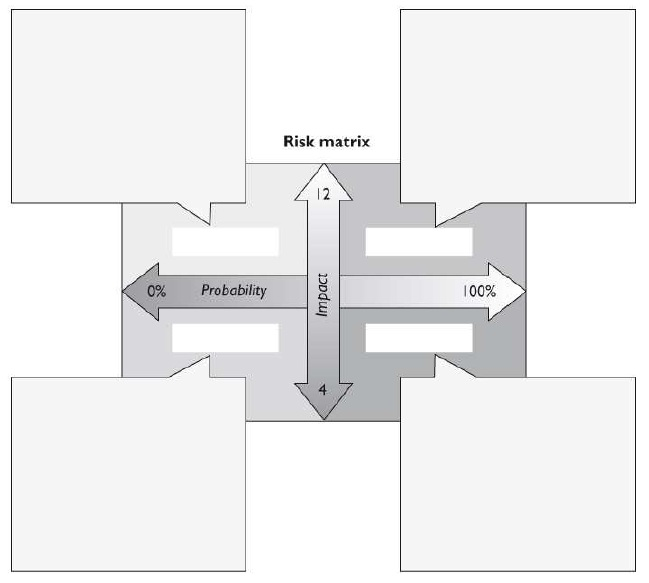
The following graphic contains a commonly used risk management scorecard. Identify the proper quadrant and its description.

A.
Top-right quadrant is high impact, low probability.
B.
Top-left quadrant is high impact, medium probability.
C.
Bottom-left quadrant is low impact, high probability.
D.
Bottom-right quadrant is low impact, high probability.
Explanation:
D: The bottom-right quadrant contains low impact, high probability risks. This means that there is a high chance that specific threats will exploit specific vulnerabilities.
Although these risks are commonly frequent, their business impact is low. Out of the four quadrants, the risks that reside in this quadrant should be dealt with after the first two
higher quadrants. An example of a risk that could reside in this quadrant is a virus that infects a user workstation. Since viruses are so common this would mean that this risk has
a high probability of taking place. This is only a user workstation and not a production system, so the impact would be low.
A is incorrect because the top-right quadrant contains high impact, high probability risks. This means that there is a high chance that specific threats will exploit specific
vulnerabilities. These risks are commonly frequent and their business impact is high. Out of the four quadrants, the risks that reside in this quadrant should be dealt with first. An
example of a risk that would reside in this quadrant is an attacker compromising an internal mail server. If the proper countermeasures are not in place, there is a high probability
that this would occur. Since this is a resource that the whole company depends upon, it would have a high business impact.
B is incorrect because the top-left quadrant contains high impact, low probability risks. This means that there is a low chance that specific threats will exploit specific
vulnerabilities. These risks are commonly infrequent and their business impact is low. Out of the four quadrants, the risks that reside in this quadrant should be dealt with after
the risks that reside in the topright quadrant. An example of this type of risk is an attacker compromising an internal DNS server. If there is an external-facing DNS server and a
DMZ is in place, an attacker being able to access an internal DNS server is low. But if this does happen, this would have a high business impact since all systems depend upon
this resource.
C is incorrect because the bottom-left quadrant contains low impact, low probability risks. This means that there is a low chance that specific threats will exploit specific
vulnerabilities. These risks are commonly infrequent and their business impact is low. Out of the four quadrants, the risks that reside in this quadrant should be dealt with after
the risks in all of the other three quadrants. An example of this type of risk would be a legacy file server that is hardly used failing and going offline. Since it is not commonly used
by users, it would have a low business impact, and if the correct countermeasures are in place, there would be a low probability of this occurring.