Which type of WAN tunneling protocol is missing from the table that follows?

A.
IPSec
B.
FDDI
C.
L2TP
D.
CSMA/CD
Explanation:
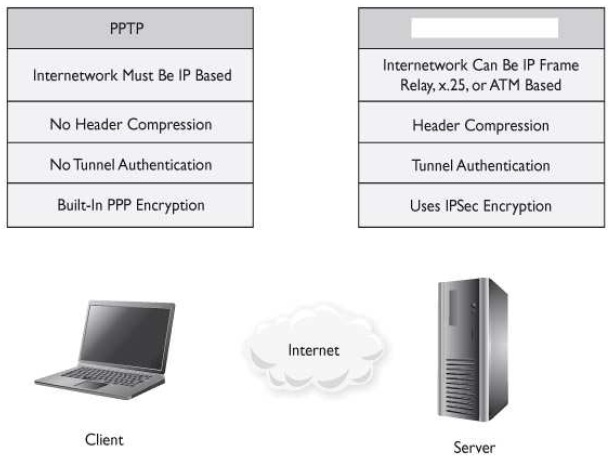
C: Tunneling is the main ingredient to a VPN because that is how the VPN creates its connection. Three main tunneling protocols are used in VPN connections: PPTP, L2TP,
and IPSec. L2TP provides the functionality of the Point-to-Point Tunneling Protocol (PPTP), but it can work over networks other than just IP, and it provides a higher level of
security when combined with IPSec. L2TP does not provide any encryption or authentication services, so it needs to be combined with IPSec if those services are required. The
processes that L2TP uses for encapsulation are similar to those used by PPTP. The PPP frame is encapsulated with L2TP. One limitation of PPTP is that it can work only over
IP networks, so other protocols must be used to move data over frame relay, X.25, and ATM links.
A is incorrect because the Internet Protocol Security (IPSec) protocol suite provides a method of setting up a secure channel for protected data exchange between two
devices. The devices that share this secure channel can be two servers, two routers, a workstation and a server, or two gateways between different networks. IPSec is a widely
accepted standard for providing network layer protection. IPSec is commonly used with L2TP to provide protection for the data that travels over this type of communication path
as shown in the graphic.
B is incorrect because Fiber Distributed Data Interface (FDDI) technology is a high-speed token-passing media access technology. FDDI has a data transmission speed of up
to 100 Mbps and is usually used as a backbone network using fiber-optic cabling. FDDI also provides fault tolerance by offering a second counter-rotating fiber ring. The primary
ring has data traveling clockwise and is used for regular data transmission. The second ring transmits data in a counterclockwise fashion and is invoked only if the primary ring
goes down. Sensors watch the primary ring and, if it goes down, invoke a ring wrap so that the data will be diverted to the second ring. Each node on the FDDI network has
relays that are connected to both rings, so if a break in the ring occurs, the two rings can be joined. L2TP is used for WAN connections, while FDDI is commonly used for MAN
connections.
C is incorrect because Carrier Sense Multiple Access with Collision Detection (CSMA/CD) is a network access method in which a carrier sensing scheme is used. A
transmission is called a carrier, so if a computer is transmitting frames, it is performing a carrier activity. When computers use the CSMA/CD protocol, they monitor the
transmission activity, or carrier activity, on the wire so they can determine when would be the best time to transmit data. Each node monitors the wire continuously and waits until
the wire is free before it transmits its data. As an analogy, consider several people gathered in a group talking here and there about this and that. If a person wants to talk, she
usually listens to the current conversation and waits for a break before she proceeds to talk. If she does not wait for the first person to stop talking, she will be speaking at the
same time as the other person, and the people around them may not be able to understand fully what each is trying to say.


Tunneling is the main ingredient to a VPN because that is how the VPN creates its connection. Three main tunneling protocols are used in VPN connections: PPTP, L2TP,
and IPSec. L2TP provides the functionality of the Point-to-Point Tunneling Protocol (PPTP), but it can work over networks other than just IP, and it provides a higher level of security when combined with IPSec. L2TP does not provide any encryption or authentication services, so it needs to be combined with IPSec if those services are required.
0
0