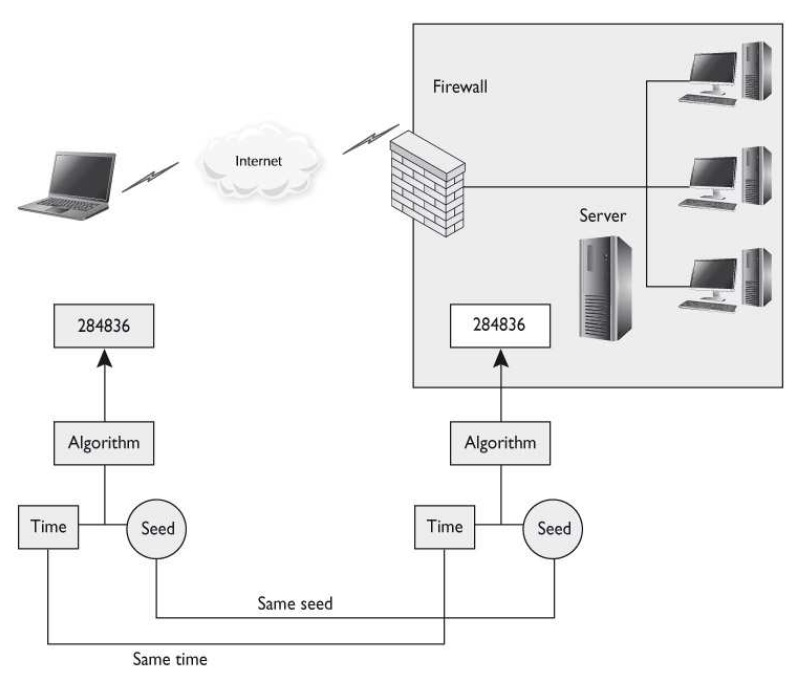
There are different ways that specific technologies can create one-time passwords for authentication purposes. What type of technology is illustrated in the graphic that follows?

A.
Counter synchronous token
B.
Asynchronous token
C.
Mandatory token
D.
Synchronous token
Explanation:
D: A synchronous token device synchronizes with the authentication service by using time or a counter as the core piece of the authentication process. If the synchronization is timebased,
as shown in this graphic, the token device and the authentication service must hold the same time within their internal clocks. The time value on the token device and a secret
key are used to create the one-time password, which is displayed to the user. The user enters this value and a user ID into the computer, which then passes them to the server running
the authentication service. The authentication service decrypts this value and compares it to the value it expected. If the two match, the user is authenticated and allowed to use the
computer and resources.
A is incorrect because if the token device and authentication service use counter-synchronization, it is not based on time as shown in the graphic. When using a countersynchronization
token device, the user will need to initiate the creation of the one-time password by pushing a button on the token device. This causes the token device and the
authentication service to advance to the next authentication value. This value and a base secret are hashed and displayed to the user. The user enters this resulting value along with a
user ID to be authenticated. In either time- or counter-based synchronization, the token device and authentication service must share the same secret base key used for encryption and
decryption.
B is incorrect because a token device using an asynchronous token-generating method employs a challenge/response scheme to authenticate the user. This technology does not
use synchronization but instead uses discrete steps in its authentication process. In this situation, the authentication server sends the user a challenge, a random value also called a
nonce. The user enters this random value into the token device, which encrypts it and returns a value the user uses as a one-time password. The user sends this value, along with a
username, to the authentication server. If the authentication server can decrypt the value and it is the same challenge value sent earlier, the user is authenticated.
C is incorrect because there is no such thing as a mandatory token. This is a distracter answer.