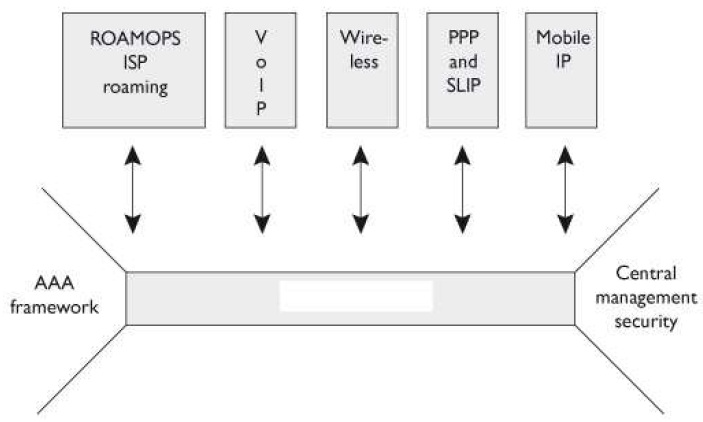
There are several different types of centralized access control protocols. Which of the following is illustrated in the graphic that follows?

A.
Diameter
B.
Watchdog
C.
RADIUS
D.
TACACS+
Explanation:
A: Diameter is an authentication, authorization, and auditing (AAA) protocol that provides the same type of functionality as RADIUS and TACACS+ but also provides more flexibility
and capabilities to meet the new demands of today’s complex and diverse networks. At one time, all remote communication took place over PPP and SLIP connections and users
authenticated themselves through PAP or CHAP. Technology has become much more complicated and there are more devices and protocols to choose from than ever before. The
Diameter protocol allows wireless devices, smart phones, and other devices to be able to authenticate themselves to networks using roaming protocols, Mobile IP, Ethernet over PPP,
Voice over IP (VoIP), and others.
B is incorrect because Watchdog timers are commonly used to detect software faults, such as a process ending abnormally or hanging. The Watchdog functionality sends out a type
of “heartbeat” packet to determine whether a service is responding. If it is not, the process can be terminated or reset. These packets help prevent against software deadlocks, infinite
loops, and process prioritization problems. This functionality can be used in AAA protocols to determine whether packets need to be re-sent and whether connections experiencing
problems should be closed and reopened, but it is not an access control protocol itself.
C is incorrect because Remote Authentication Dial-In User Service (RADIUS) is a network protocol and provides client/server authentication, authorization, and audit for remote
users. A network may have access servers, DSL, ISDN, or a T1 line dedicated for remote users to communicate through. The access server requests the remote user’s logon
credentials and passes them back to a RADIUS server, which houses the usernames and password values. The remote user is a client to the access server, and the access server is a
client to the RADIUS server.
D is incorrect because TACACS+ provides basically the same functionality as RADIUS. The RADIUS protocol combines the authentication and authorization functionality. TACACS+
uses a true authentication, authorization, accounting, and audit (AAA) architecture, which separates each function out. This gives a network administrator more flexibility in how remote
users are authenticated. Neither TACACS+ or RADIUS can carry out these services for devices that need to communicate over VoIP, mobile IP, or other types of the similar types of
protocols.