There are several different important pieces to the Common Criteria. Which of the following best describes the first of the missing components?

A.
Target of evaluation
B.
Protection profile
C.
Security target
D.
EALs
Explanation:
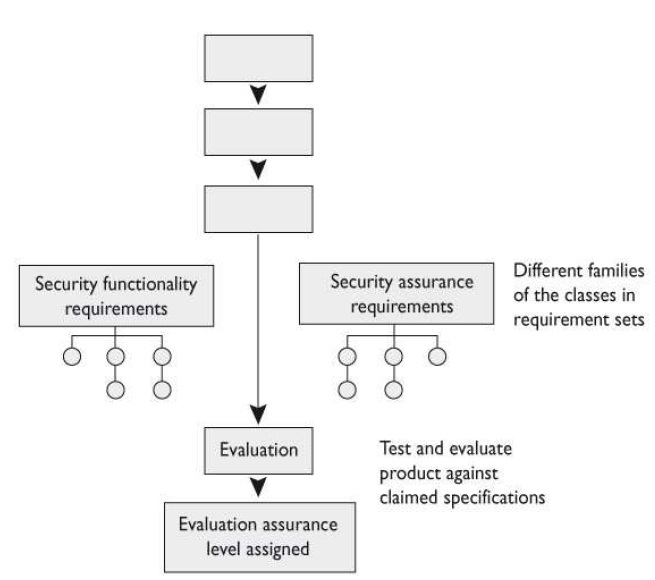
B: The Common Criteria use protection profiles in its evaluation process. This is a mechanism used to describe a real-world need of a product that is not currently on
the market. The protection profile contains the set of security requirements, their meaning and reasoning, and the corresponding EAL rating that the intended product
will require. The protection profile describes the environmental assumptions, the objectives, and the functional and assurance-level expectations. Each relevant threat is
listed, along with how it is to be controlled by specific objectives. The protection profile also justifies the assurance level and requirements for the strength of each
protection mechanism that is expected to be in the new product. The protection profile basically says, “This is what we need out of a new product.”
A is incorrect because the target of evaluation (ToE), the second of the three missing pieces in the graphic, is the actual product that is being evaluated against the
Common Criteria. Where the protection profile states, “This is what we need out of a new product,” the ToE is the product that a vendor creates to meet the
requirements outlined in the protection profile. When there is a need in the industry for a new product that provides specific functionality and security, someone develops
the protection profile to outline this need. A vendor fulfills the need by creating a new product, referred to as the ToE.
C is incorrect because the security target, the third piece missing in the graphic, is the vendor’s written explanation of the security functionality and assurance
mechanisms that meet the needed solution outlined in the protection profile and fulfilled by the target of evaluation (ToE). Where the protection profile outlines, “This is
what we need,” the ToE is the product that fulfills this need, and the security target is the explanation on how this ToE is mapped to the protection profile. The evaluators
compare the ToE with these three constructs, along with the actual requirements of the Common Criteria before assigning it an Evaluation Assurance Level.
D is incorrect because evaluation assurance levels (EALs) outline the assurance ratings used in the Common Criteria. It is basically the grading system used in these
criteria to describe the assurance and security required by a specific product. When an evaluator evaluates a product, after all of her tests she will she assign an EAL
value. This value is basically the grade that the product receives after all of the tests it is put through. The Common Criteria uses a different assurance rating system
than the previously used criteria. It has packages of specifications that must be met for a product to obtain the corresponding rating. These ratings and pack- ages are
collectively called the EALs. Once a product achieves any type of rating, customers can view this information on an Evaluated Products List (EPL) to understand which
product provides the most security assurance. So if you are going to purchase a product and you have a certain security assurance specification that the product must
meet, you can view the EPL to see what maps to your needs.


The Common Criteria use protection profiles in its evaluation process. This is a mechanism used to describe a real-world need of a product that is not currently on
the market. The protection profile contains the set of security requirements, their meaning and reasoning, and the corresponding EAL rating that the intended product
will require. The protection profile describes the environmental assumptions, the objectives, and the functional and assurance-level expectations. Each relevant threat is listed, along with how it is to be controlled by specific objectives.
通用準則使用保護輪廓在其評估過程。這是用於描述真實世界需要的產品,是不是目前市場上的機構。保護配置文件包含該組的安全要求,其含義和推理,以及相應的EAL額定值所需產物將需要。保護個人資料介紹了環境的假設,目標,功能和保證級的預期。各相關威脅上市,它是如何通過具體的目標來控制沿。
0
0