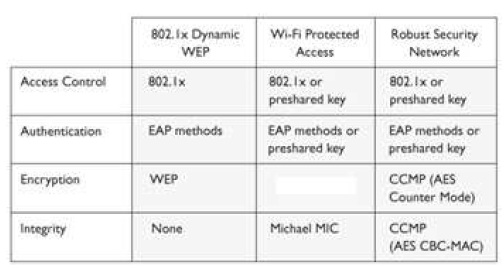
What type of security encryption component is missing from the table that follows?

A.
Service Set ID
B.
Temporal Key Integrity Protocol
C.
Ad hoc WLAN
D.
Open system authentication
Explanation:
B: The Temporal Key Integrity Protocol (TKIP) generates random values used in the encryption process, which makes it much harder for an attacker to break. To allow for an
even higher level of encryption protection, the standard also includes the new Advanced Encryption Standard (AES) algorithm to be used in new WLAN implementations. TKIP
actually works with the wired equivalent privacy (WEP) protocol by feeding it keying material, which is data to be used for generating new dynamic keys. WEP uses the RC4
encryption algorithm, and the current implementation of the algorithm provides very little protection. More complexity is added to the key generation process with the use of TKIP,
which makes it much more difficult for attackers to uncover the encryption keys. The IEEE working group developed TKIP so that customers would only need to obtain firmware
or software updates instead of purchasing new equipment for this type of protection.
A is incorrect because when wireless devices work in infrastructure mode, the access point (AP) and wireless clients form a group referred to as a Basic Service Set (BSS).
This group is assigned a name, which is the Service Set ID (SSID) value. This value has nothing to do with encryption. Any hosts that wish to participate within a particular
WLAN must be configured with the proper SSID. Various hosts can be segmented into different WLANs by using different SSIDs. The reasons to segment a WLAN into portions
are the same reasons wired systems are segmented on a network: the users require access to different resources, have different business functions, or have different levels of
trust.
C is incorrect because an ad hoc WLAN has nothing to do with encryption, but rather with how wireless devices on a network are set up. An ad hoc WLAN has no access
points; the wireless devices communicate with each other through their wireless NICs instead of going through a centralized device. To construct an ad hoc network, wireless
client software is installed on contributing hosts and configured for peer-to-peer operation mode.
D is incorrect because open system authentication (OSA) just means a wireless device does not need to prove it has a specific cryptographic key for authentication.
Depending upon the product and the configuration, a network administrator can also limit access to specific MAC addresses. OSA does not require the wireless device to prove
to an access point it has a specific cryptographic key to allow for authentication purposes. In many cases, the wireless device needs to provide only the correct SSID value. In
OSA implementations, all transactions are in clear text because no encryption is involved. So an intruder can sniff the traffic, capture the necessary steps of authentication, and
walk through the same steps to be authenticated and associated to an AP.


The Temporal Key Integrity Protocol (TKIP) generates random values used in the encryption process, which makes it much harder for an attacker to break. To allow for an even higher level of encryption protection, the standard also includes the new Advanced Encryption Standard (AES) algorithm to be used in new WLAN implementations. TKIPactually works with the wired equivalent privacy (WEP) protocol by feeding it keying material, which is data to be used for generating new dynamic keys. WEP uses the RC4 encryption algorithm, and the current implementation of the algorithm provides very little protection. More complexity is added to the key generation process with the use of TKIP, which makes it much more difficult for attackers to uncover the encryption keys. The IEEE working group developed TKIP so that customers would only need to obtain firmware or software updates instead of purchasing new equipment for this type of protection.
臨時密鑰完整性協議(TKIP)產生在加密過程中,這使得它更難攻擊者破壞用於隨機值。以允許加密保護的一個更高的水平,該標準還包括在新的VLAN實現要使用的新的高級加密標準(AES)算法。 TKIP實際餵養它的密鑰材料,它是用於生成新的動態密鑰數據與有線等效保密(WEP)協議工作。 WEP使用RC4加密算法,目前執行的算法提供了非常少的保護。更複雜被添加到密鑰生成過程與使用TKIP的,這使得它更難以攻擊者發現加密密鑰。在IEEE工作組制定了TKIP,使客戶只需要獲取固件或軟件更新,而不是購買新設備為這種類型的保護。
0
0