Your network contains an Active Directory forest named contoso.com. The forest contains two
domains named contoso.com and childl.contoso.com. The domains contain three domain
controllers.
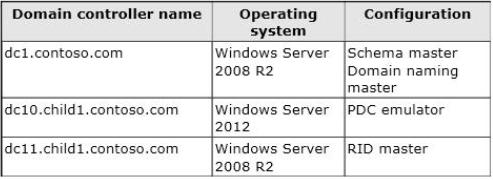
The domain controllers are configured as shown in the following table.
You need to ensure that the KDC support for claims, compound authentication, and kerberos
armoring setting is enforced in the child1.contoso.com domain.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose
two.)

A.
Upgrade DC1 to Windows Server 2012 R2.
B.
Upgrade DC11 to Windows Server 2012 R2.
C.
Raise the domain functional level of childl.contoso.com.
D.
Raise the domain functional level of contoso.com.
E.
Raise the forest functional level of contoso.com.
Explanation:
The root domain in the forest must be at Windows Server 2012 level. First upgrade DC1 to this level
(A), then raise the contoso.com domain functional level to Windows Server 2012 (D).
* (A) To support resources that use claims-based access control, the principal’s domains will need to
be running one of the following:
/ All Windows Server 2012 domain controllers
/ Sufficient Windows Server 2012 domain controllers to handle all the Windows 8 device
authentication requests
/ Sufficient Windows Server 2012 domain controllers to handle all the Windows Server 2012
resource protocol transition requests to support non-Windows 8 devices.
What’s New in Kerberos Authentication
http://technet.microsoft.com/en-us/library/hh831747.aspx.


Why would you rise domain function level in the parent when: “You need to ensure that the KDC support for claims, compound authentication, and kerberos
armoring setting is enforced in the child1.contoso.com domain”
I’d say B and C
4
0
I say B & C, too
2
1
I think you cannot raise a child domains functional level and leave the regular domain at a lower level. Which means the answer is correct
0
4
I’d say you are wrong as the provided answer is.
reasons:
1. https://technet.microsoft.com/en-us/library/understanding-active-directory-functional-levels(v=ws.10) states that “You can set the domain functional level to a value that is higher than the forest functional level. For example, if the forest functional level is Windows Server 2003, you can set the domain functional level to Windows Server 2003or higher.”
2. the question was not about what to do first (like some other questions are), but what to do. So why not just raise the sub domain’s functional level by performing B) and C) and don’t care the forest level…?
B) + C)
3
0
https://technet.microsoft.com/windows-server-docs/identity/ad-ds/deploy/upgrade-domain-controllers-to-windows-server-2012-r2-and-windows-server-2012#BKMK_FunctionalLevels
0
0
https://technet.microsoft.com/windows-server-docs/identity/ad-ds/deploy/install-a-new-windows-server-2012-active-directory-child-or-tree-domain–level-200-
You must also specify a Domain functional level. The default functional level is Windows Server 2012, and you can choose any other value that is equal to or greater than the current forest functional level.
0
0
From social.technet.microsoft.com
“Domain and Forest functional levels are almost separate. You will see what I mean by almost.
Domain are boundaries that can be raised independently of other domains and the forest in which it is located. For a forest to be raised to the the latest, all domains must be at that level – that is what I meant by almost separate.”
Answer: B,C
0
0
B, C
0
0
p.s.
Free 391q dumps from Google Drive:
https://drive.google.com/open?id=0B-ob6L_QjGLpfm94alk1eU9xWjFYRkVoNkl0cjRiOXZRRjVkUXNXTklicDdKZDJwRGJCM1k
0
3
Ok, I’m confused.
From: https://technet.microsoft.com/en-us/library/hh831747(v=ws.11).aspx
“When the supported (or higher) setting is configured, domain controllers running Windows Server 2012, Windows Server 2008 R2, or Windows Server 2008 will advertise domain support for claims and compound authentication for Dynamic Access Control and Kerberos armoring.”
So, if Claims, Compound and Armoring are supports on 2008 and later, why are we upgrading DC1?
0
0
I’d go B and C.
https://technet.microsoft.com/en-us/library/hh831747(v=ws.11).aspx
“Windows Server 2012 domain controllers are configured for supporting claims and compound authentication for Dynamic Access Control and Kerberos armoring option which requires Windows Server 2012 domain functional level and the domain is not at this level.”
“To support resources that use claims-based access control, the principal’s domains will need to be running one of the following:
All Windows Server 2012 domain controllers ”
As the principal should be child1.contoso.com, then the child1.contoso.com DCs should all be 2012.
0
0
Good note Farku
0
0
But Answer A+E or A+D
I would say A+D because we can’t have windows server 2008 (dc11) in a 2012 forest functional level
0
0
It is A+E
A because:If you want to create access control based on claims and compound authentication, you need to deploy Dynamic Access Control. This requires that you upgrade to Kerberos clients and use the KDC, which support these new authorization types. With Windows Server 2012, you do not have to wait until all the domain controllers and the domain functional level are upgraded to take advantage of new access control options.
https://social.technet.microsoft.com/Forums/windowsserver/en-US/1ab3eca9-6d8a-4117-a289-00af159186c3/kdc-support-for-claims-compound-authentication-and-kerberos-armoring-is-ws-2012-domain?forum=winserver8gen
E Because A , and therefor this : https://technet.microsoft.com/en-us/library/cc730985(v=ws.11).aspx
Do not raise the forest functional level higher if you have or will have any domain controllers running an earlier version of Windows Server.
0
1
You would not be able to upgrade the forest functional level if you still have a DC (in this case, DC11) running an earlier version.
For this particular question, I think the answer is B and C. We only need this to function in the child1.contoso.com and to do that, we need a server running 2012 and a domain functional level as well.
0
0
Devices running Windows 8 will fail authentication if they cannot find a domain controller running Windows Server 2012 . It is important to ensure that there are sufficient domain controllers running Windows Server 2012 for any account, referral, and resource domains that are supported.
Although the enforcement needs to be ensured for child1 in this scenario, it sounds like EACH DOMAIN must have at least one 2012 DC running.
However, when sticking to the “facts, just the facts” mentality of the scenario, the features are limited when domain functional level is not Windows Server 2012 as stated:
Always provide claims and Fail unarmored authentication requests options cause intermittent authentication or access control failures if there are any domain controllers not running -Windows Server 2012 in the domain. So neither of these options will take effect until the domain is set at the Windows Server 2012 functional level. Until then, domain controllers running Windows Server 2012 will behave as if the Supported option is configured.
B & C is the most appropriate response
0
0