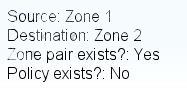
Which option is the resulting action in a zone-based policy firewall configuration with these
conditions?

A.
no impact to zoning or policy
B.
no policy lookup (pass)
C.
drop
D.
apply default policy
Explanation:
http://www.cisco.com/en/US/docs/ios-xml/ios/sec_data_zbf/configuration/xe-3s/sec-zone-polfw.html
Zone Pairs
A zone pair allows you to specify a unidirectional firewall policy between two security zones.
To define a zone pair, use the zone-pair security command. The direction of the traffic is specified
by source and destination zones. The source and destination zones of a zone pair must be
security zones.
You can select the default or self zone as either the source or the destination zone. The self zone
is a systemdefined zone which does not have any interfaces as members. A zone pair that
includes the self zone, along with the associated policy, applies to traffic directed to the device or
traffic generated by the device. It does not apply to traffic through the device.
The most common usage of firewall is to apply them to traffic through a device, so you need at
least two zones (that is, you cannot use the self zone).
To permit traffic between zone member interfaces, you must configure a policy permitting (or
inspecting) traffic between that zone and another zone. To attach a firewall policy map to the
target zone pair, use the servicepolicy type inspect command.
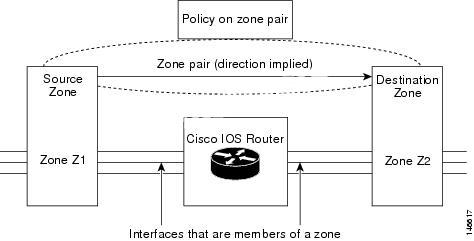
The figure below shows the application of a firewall policy to traffic flowing from zone Z1 to zone
Z2, which means that the ingress interface for the traffic is a member of zone Z1 and the egressinterface is a member of zone Z2.
Figure 2. Zone PairsIf there are two zones and you require policies for traffic going in both directions (from Z1 to Z2
and Z2 to Z1), you must configure two zone pairs (one for each direction).
If a policy is not configured between zone pairs, traffic is dropped. However, it is not necessary to
configure a zone pair and a service policy solely for the return traffic. By default, return traffic is not
allowed. If a service policy inspects the traffic in the forward direction and there is no zone pair and
service policy for the return traffic, the return traffic is inspected. If a service policy passes the
traffic in the forward direction and there is no zone pair and service policy for the return traffic, the
return traffic is dropped. In both these cases, you need to configure a zone pair and a service
policy to allow the return traffic. In the above figure, it is not mandatory that you configure a zone
pair source and destination for allowing return traffic from Z2 to Z1. The service policy on Z1 to Z2
zone pair takes care of it.