What are two primary attack methods of VLAN hopping? (Choose two.)

A.
VoIP hopping
B.
switch spoofing
C.
CAM-table overflow
D.
double tagging
Explanation:
There are a number of different types of VLAN attacks in modern switched networks. The VLAN
architecture simplifies network maintenance and improves performance, but it also opens the door
to abuse. It is important to understand the general methodology behind these attacks and the
primary approaches to mitigate them.
VLAN hopping enables traffic from one VLAN to be seen by another VLAN. Switch spoofing is a
type of VLAN hopping attack that works by taking advantage of an incorrectly configured trunk
port. By default, trunk ports have access to all VLANs and pass traffic for multiple VLANs across
the same physical link, generally between switches.
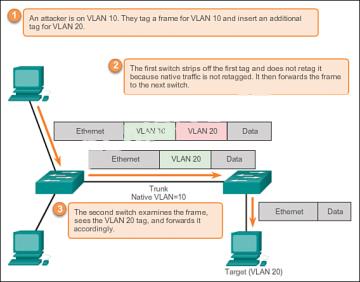
Another type of VLAN attack is a double-tagging(or double-encapsulated) VLAN hopping attack.
This type of attack takes advantage of the way that hardware on most switches operates. Most
switches perform only one level of 802.1Q de-encapsulation, which allows an attacker to embed a
hidden 802.1Q tag inside the frame. This tag allows the frame to be forwarded to a VLAN that the
original 802.1Q tag did not specify as shown below. An important characteristic of the doubleencapsulated VLAN hopping attack is that it works even if trunk ports are disabled, because a host
typically sends a frame on a segment that is not a trunk link.Double-Tagging Attack
Reference: http://www.ciscopress.com/articles/article.asp?p=2181837&seqNum=10