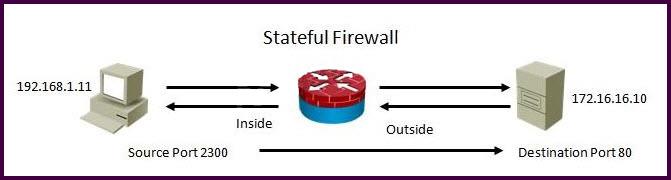
Refer to the exhibit.
Using a stateful packet firewall and given an inside ACL entry of permit ip 192.16.1.0 0.0.0.255
any, what would be the resulting dynamically configured ACL for the return traffic on the outside
ACL?

A.
permit tcp host 172.16.16.10 eq 80 host 192.168.1.11 eq 2300
B.
permit ip 172.16.16.10 eq 80 192.168.1.0 0.0.0.255 eq 2300
C.
permit tcp any eq 80 host 192.168.1.11 eq 2300
D.
permit ip host 172.16.16.10 eq 80 host 192.168.1.0 0.0.0.255 eq 2300
Explanation:
http://www.cisco.com/en/US/docs/security/security_management/cisco_security_manager/security
_manager/4.1/user/guide/fwinsp.html
Understanding Inspection Rules
Inspection rules configure Context-Based Access Control (CBAC) inspection commands. CBAC
inspects traffic that travels through the device to discover and manage state information for TCP
and UDP sessions. The device uses this state information to create temporary openings to allow
return traffic and additional data connections for permissible sessions.
CBAC creates temporary openings in access lists at firewall interfaces. These openings are
created when inspected traffic exits your internal network through the firewall. The openings allow
returning traffic (that would normally be blocked) and additional data channels to enter your
internal network back through the firewall. The traffic is allowed back through the firewall only if it
is part of the same session as the original traffic that triggered inspection when exiting through the
firewall.
Inspection rules are applied after your access rules, so any traffic that you deny in the access rule
is not inspected. The traffic must be allowed by the access rules at both the input and output
interfaces to be inspected. Whereas access rules allow you to control connections at layer 3
(network, IP) or 4 (transport, TCP or UDP protocol), you can use inspection rules to control traffic
using application-layer protocol session information.
For all protocols, when you inspect the protocol, the device provides the following functions:
•Automatically opens a return path for the traffic (reversing the source and destination addresses),
so that you do not need to create an access rule to allow the return traffic. Each connection is
considered a session, and the device maintains session state information and allows return traffic
only for valid sessions. Protocols that use TCP contain explicit session information, whereas for
UDP applications, the device models the equivalent of a session based on the source and
destination addresses and the closeness in time of a sequence of UDP packets.
These temporary access lists are created dynamically and are removed at the end of a session.
•Tracks sequence numbers in all TCP packets and drops those packets with sequence numbers
that are not within expected ranges.
•Uses timeout and threshold values to manage session state information, helping to determine
when to drop sessions that do not become fully established. When a session is dropped, or reset,
the device informs both the source and destination of the session to reset the connection, freeing
up resources and helping to mitigate potential Denial of Service (DoS) attacks.