DRAG DROP
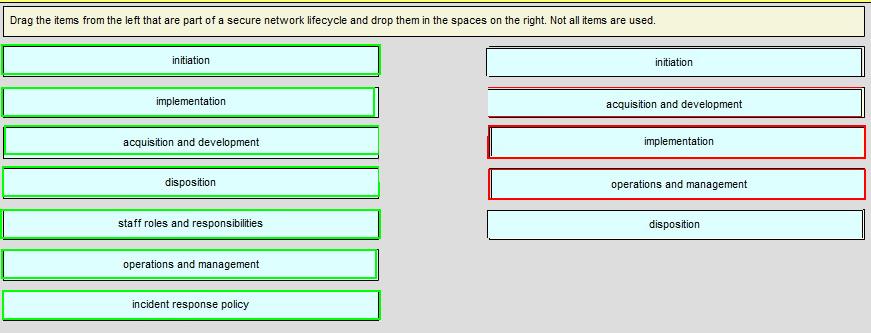
Drag the items from the left that are part of a secure network lifecycle and drop them in the spaces on the right.

Explanation:
1. Initiation
2. Acquisition and development
3. Implementation
4. Operations and maintenance
5. Disposition
Secure Network Life Cycle
By framing security within the context of IT governance, compliance, and risk management, and
by building it with a sound security architecture at its core, the result is usually a less expensiveand more effective process. Including security early in the information process within the system
design life cycle (SDLC) usually results in less-expensive and more-effective security when
compared to adding it to an operational system.
A general SDLC includes five phases:
1. Initiation
2. Acquisition and development
3. Implementation
4. Operations and maintenance
5. Disposition
Each of these five phases includes a minimum set of security steps that you need to follow to
effectively incorporate security into a system during its development. An organization either uses
the general SDLC or develops a tailored SDLC that meets its specific needs. In either case, the
National Institute of Standards and Technology (NIST) recommends that organizations incorporate
the associated IT security steps of this general SDLC into their development process.