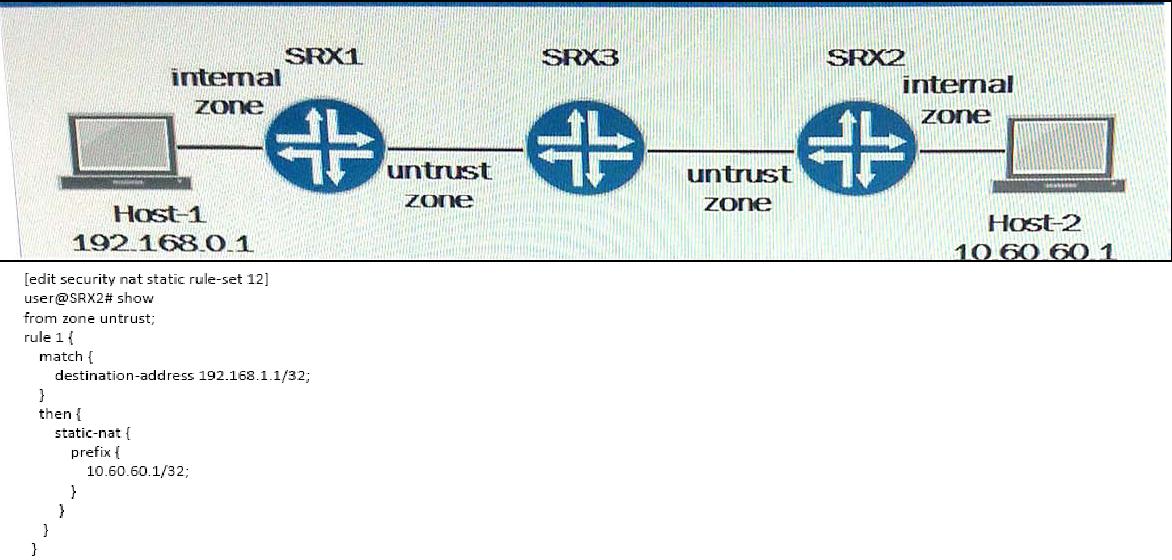
Click the Exhibit button. Host-2 initiates communication with Host-1. All other routing and
policies are in place to allow the traffic. What is the result of the communication?

A.
No translation occurs.
B.
The 10.60.60.1 address is translated to the 192.168.1.1 address.
C.
The 192.168.0.1 address is translated to the 10.60.60.1 address.
D.
The 192.168.0.1 address is translated to the 192.168.1.1 address.


HOW THE ANSWER IS B !!??!!?? HOW ??!
it says in NAT >> 192.168.1.1/32 !! and host 1 is 0.1 ..
0
0
Hey Juniper,
think about it .. static NAT is bidirectional ..
Static NAT is a 1:1 bidirectional NAT that maps one IP address to another. For instance, in the trust zone the IP address might be 1.1.1.1, but when it goes out the untrust zone, it will be mapped to 2.2.2.2. Because this NAT is bidirectional, if the traffic comes in the reverse direction, it will be mapped from 2.2.2.2 to 1.1.1.1, security policy permitting. This means that you don’t need to manually create a reverse NAT entry for this mapping
0
0
What is true answer?
0
0
It should be A….
0
0
Answer:B
When Host-2 initiates communication with Host-1, Host-2 IP address 10.60.60.1 will be translated to 192.168.1.1 address as per that static NAT statement on SRX2.
0
0
It makes sense to be “B”, but if you pay attention, the directional context is from zone Untrust on SRX2. Host-2 initiates communication, and it start from internal zone to untrust zone, not matching the NAT rule.
I guess this is “A”.
Someone?
0
0
so A or B ?
0
0
A is Correct.
1.> Host IP and Static NAT prefix 10.60.60.1 are same so no translation will occur
2.> Host-2 (10.60.60.1) will communicate with Host-1 (192.168.0.1)
However rule-set says match destination “192.168.1.1” so NAT rules should not process.
0
0
B 100%. All those who claim A – go reread AJSEC course, NAT section.
0
0
B 100%. Tested this in my lab.
vSRX(10.10.11.1)——-(10.10.11.2)ge-0/0/0.0_vSRX-1_ge-0/0/1.0(10.0.1.3)—–(10.0.1.150)centos
root@vSRX-1> show configuration security nat
static {
rule-set snat {
from zone vpn;
rule 1 {
match {
destination-address 10.10.11.2/32;
}
then {
static-nat {
prefix {
10.0.1.150/32;
}
}
}
}
}
}
# Ping from centos to vSRX:
root@vSRX-1> show security flow session
Session ID: 139502, Policy name: permit/6, Timeout: 4, Valid
In: 10.0.1.150/10 –> 10.10.11.1/17873;icmp, Conn Tag: 0x0, If: ge-0/0/1.0, Pkts: 1, Bytes: 84,
Out: 10.10.11.1/17873 –> 10.10.11.2/10;icmp, Conn Tag: 0x0, If: ge-0/0/0.0, Pkts: 1, Bytes: 84,
# First packet:
Dec 4 11:07:58 11:07:58.635261:CID-0:THREAD_ID-01:RT:10.10.11.1/17683;1> matched filter icmptest:
Dec 4 11:07:58 11:07:58.635271:CID-0:THREAD_ID-01:RT:packet [84] ipid = 28022, @0x99731ece
Dec 4 11:07:58 11:07:58.635275:CID-0:THREAD_ID-01:RT:—- flow_process_pkt: (thd 1): flow_ctxt type 15, common flag 0x0, mbuf 0x68e25a00, rtbl_idx = 0
Dec 4 11:07:58 11:07:58.635287:CID-0:THREAD_ID-01:RT: no session found, start first path. in_tunnel – 0x0, from_cp_flag – 0
Dec 4 11:07:58 11:07:58.635292:CID-0:THREAD_ID-01:RT: flow_first_create_session
Dec 4 11:07:58 11:07:58.635302:CID-0:THREAD_ID-01:RT: flow_first_in_dst_nat: in , out dst_adr 10.10.11.1, sp 1, dp 17683
Dec 4 11:07:58 11:07:58.635303:CID-0:THREAD_ID-01:RT: chose interface ge-0/0/1.0 as incoming nat if.
Dec 4 11:07:58 11:07:58.635307:CID-0:THREAD_ID-01:RT:flow_first_rule_dst_xlate: DST no-xlate: 0.0.0.0(0) to 10.10.11.1(17683) << zone vpn (0x0,0x14513,0x4513)
Dec 4 11:07:58 11:07:58.635341:CID-0:THREAD_ID-01:RT:Policy lkup: vsys 0 zone(7:trust) -> zone(6:vpn) scope:0
Dec 4 11:07:58 11:07:58.635341:CID-0:THREAD_ID-01:RT: 10.0.1.150/2048 -> 10.10.11.1/15802 proto 1
Dec 4 11:07:58 11:07:58.635379:CID-0:THREAD_ID-01:RT: permitted by policy permit(6)
Dec 4 11:07:58 11:07:58.635380:CID-0:THREAD_ID-01:RT: packet passed, Permitted by policy.
Dec 4 11:07:58 11:07:58.635383:CID-0:THREAD_ID-01:RT: reverse mip xlate 10.0.1.150/1 -> 10.10.11.2/1 (on ge-0/0/0.0)
Dec 4 11:07:58 11:07:58.635384:CID-0:THREAD_ID-01:RT:flow_first_src_xlate: nat_src_xlated: True, nat_src_xlate_failed: False
Dec 4 11:07:58 11:07:58.635386:CID-0:THREAD_ID-01:RT:flow_first_src_xlate: hip xlate: 10.0.1.150->10.10.11.2 at ge-0/0/0.0 (vs. ge-0/0/0.0)
Dec 4 11:07:58 11:07:58.635387:CID-0:THREAD_ID-01:RT: dip id = 0/0, 10.0.1.150/1->10.10.11.2/1 protocol 0
Dec 4 11:07:58 11:07:58.635389:CID-0:THREAD_ID-01:RT: choose interface ge-0/0/0.0(P2P) as outgoing phy if
Dec 4 11:07:58 11:07:58.635393:CID-0:THREAD_ID-01:RT:is_loop_pak: No loop: on ifp: ge-0/0/0.0, addr: 10.10.11.1, rtt_idx:0
Dec 4 11:07:58 11:07:58.635448:CID-0:THREAD_ID-01:RT:flow_first_complete_session: pak_ptr is xlated packet
Dec 4 11:07:58 11:07:58.635461:CID-0:THREAD_ID-01:RT:flow_ipv4_rt_lkup success 10.0.1.150, iifl 0x49, oifl 0x49
Dec 4 11:07:58 11:07:58.635463:CID-0:THREAD_ID-01:RT: route lookup: dest-ip 10.0.1.150 orig ifp ge-0/0/1.0 output_ifp ge-0/0/1.0 orig-zone 7 out-zone 7 vsd 0
Dec 4 11:07:58 11:07:58.635464:CID-0:THREAD_ID-01:RT: route to 10.0.1.150
Dec 4 11:07:58 11:07:58.635468:CID-0:THREAD_ID-01:RT:no need update ha
Dec 4 11:07:58 11:07:58.635469:CID-0:THREAD_ID-01:RT:Installing c2s NP session wing
Dec 4 11:07:58 11:07:58.635470:CID-0:THREAD_ID-01:RT:Installing s2c NP session wing
Dec 4 11:07:58 11:07:58.635477:CID-0:THREAD_ID-01:RT:first path session installation succeeded
Dec 4 11:07:58 11:07:58.635477:CID-0:THREAD_ID-01:RT: flow got session.
Dec 4 11:07:58 11:07:58.635478:CID-0:THREAD_ID-01:RT: flow session id 139502
Dec 4 11:07:58 11:07:58.635485:CID-0:THREAD_ID-01:RT: post addr xlation: 10.10.11.2->10.10.11.1.
Dec 4 11:07:58 11:07:58.635486:CID-0:THREAD_ID-01:RT: post addr xlation: 10.10.11.2->10.10.11.1.
Dec 4 11:07:58 11:07:58.635487:CID-0:THREAD_ID-01:RT:skip pre-frag: is_tunnel_if- 0, is_if_mtu_configured- 0
Dec 4 11:07:58 11:07:58.635488:CID-0:THREAD_ID-01:RT:mbuf 0x68e25a00, exit nh 0xe0010
Dec 4 11:07:58 11:07:58.635489:CID-0:THREAD_ID-01:RT: —– flow_process_pkt rc 0x0 (fp rc 0)
# Return packet:
Dec 4 11:07:58 11:07:58.635977:CID-0:THREAD_ID-01:RT:10.10.11.2/1;1> matched filter icmptest:
Dec 4 11:07:58 11:07:58.635979:CID-0:THREAD_ID-01:RT:packet [84] ipid = 28022, @0x9811dece
Dec 4 11:07:58 11:07:58.635980:CID-0:THREAD_ID-01:RT:—- flow_process_pkt: (thd 1): flow_ctxt type 15, common flag 0x0, mbuf 0x68d75000, rtbl_idx = 0
Dec 4 11:07:58 11:07:58.635981:CID-0:THREAD_ID-01:RT: flow process pak fast ifl 72 in_ifp ge-0/0/0.0
Dec 4 11:07:58 11:07:58.635983:CID-0:THREAD_ID-01:RT: ge-0/0/0.0:10.10.11.1->10.10.11.2, icmp, (0/0)
Dec 4 11:07:58 11:07:58.635985:CID-0:THREAD_ID-01:RT: find flow: table 0x20669740, hash 28135(0xffff), sa 10.10.11.1, da 10.10.11.2, sp 17683, dp 1, proto 1, tok 6, conn-tag 0x00000000
Dec 4 11:07:58 11:07:58.635990:CID-0:THREAD_ID-01:RT: flow got session.
Dec 4 11:07:58 11:07:58.635990:CID-0:THREAD_ID-01:RT: flow session id 139502
Dec 4 11:07:58 11:07:58.635995:CID-0:THREAD_ID-01:RT: post addr xlation: 10.10.11.1->10.0.1.150.
Dec 4 11:07:58 11:07:58.635997:CID-0:THREAD_ID-01:RT: post addr xlation: 10.10.11.1->10.0.1.150.
Dec 4 11:07:58 11:07:58.636000:CID-0:THREAD_ID-01:RT: —– flow_process_pkt rc 0x0 (fp rc 0)
0
0
Passed JN0-633 exam recently!
65 multiple choice questions, a little difficult to pass.
Pay close attention to questions on AppQoS, Routing (OSPF, BGP) in VPN (group, auto and hub-and-spoke), AppSecure, troubleshoot of IPSec, etc.
I learned valid JN0-633 dumps here:
http://www.passleader.com/jn0-633.html (209Q VCE and PDF)
Recommend to you!
0
0
P.S.
You can download that 209Q dumps for free, here:
https://doc.co/Tek7cT
Good Luck!
0
0
Hi Francisco DE,
The link you posted got 156 questions and not 209. Please explain. Thanks.
0
0