The Wireless Transport Layer Security Protocol (WTLS) in the Wireless Application Protocol (WAP)
stack provides for security:

A.
Between the Internet and the content server
B.
Between the WAP content server and the WAP client
C.
Between the WAP gateway and the content server
D.
Between the WAP client and the gateway
Explanation:
Transport Layer Security (TLS) provides for security between the content server on the Internet and
the WAP gateway. (Answer “Between the WAP gateway and the content server” is, thus, incorrect.)
Similarly, WTLS provides security between the WAP mobile device (client software) and the WAP
gateway. Since WAP cannot interface directly with the Internet, all WAP information has to be
converted to HTTP in the WAP gateway to enable it to exchange information with the Internet
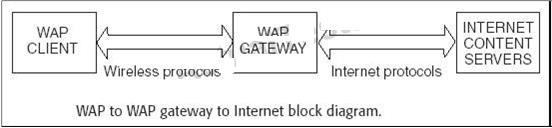
content servers. The simple block diagram illustrates these concepts. Exhibit:A vulnerability occurs since data encrypted with wireless protocols has to be decrypted in the WAP
gateway and then re-encrypted with the Internet protocols. This process is reversed when data flows
from the Internet content servers to the WAP client. Thus, the information is vulnerable while it is in
the decrypted state on the WAP gateway. This condition is known as the WAP Gap. In order to
address this issue, the WAP Forum has put forth specifications that will reduce this vulnerability and,
thus, support e-commerce applications. These specifications are defined in WAP 1.2 as WMLScript
Crypto Library and the WAP Identity Module (WIM). The WMLScript Crypto Library supports end-toend security by providing for cryptographic functions to be initiated on the WAP client from the
Internet content server. These functions include digital signatures originating with the WAP client
and encryption and decryption of data. The WIM is a tamper-resistant device, such as a smart card,
that cooperates with WTLS and provides cryptographic operations during the handshake phase. The
WAP Forum is also considering another alternative to providing the end-to-end encryption for WAP.
This alternative, described in WAP specification 1.3, is the use of a client proxy server that
communicates authentication and authorization information to the wireless network server.
*Answer “Between the Internet and the content server” is incorrect since the content server is on
the Internet side of the communication and answer “Between the WAP content server and the WAP
client” assumes a direct interface between the content server and the client without going through
the necessary Internet and wireless protocols.