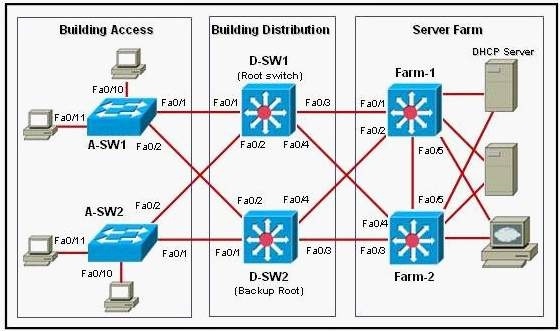
Refer to the exhibit. An attacker is connected to interface Fa0/11 on switch A-SW2 and attempts to establish a DHCP server for a man-in-middle attack. Which recommendation, if followed, would mitigate this type of attack?

A.
All switch ports in the Building Access block should be configured as DHCP untrusted ports.
B.
All switch ports in the Building Access block should be configured as DHCP trusted ports.
C.
All switch ports connecting to servers in the Server Farm block should be configured as DHCP untrusted ports.
D.
All switch ports connecting to hosts in the Building Access block should be configured as DHCP trusted ports.
E.
All switch ports in the Server Farm block should be configured as DHCP untrusted ports.
F.
All switch ports connecting to hosts in the Building Access block should be configured as DHCP untrusted ports.
Explanation:
One of the ways that an attacker can gain access to network traffic is to spoof responses that would be sent by a valid DHCP server. The DHCP spoofing device replies to client DHCP requests. The legitimate server may reply also, but if the spoofing device is on the same segment as the client, its reply to the client may arrive first. The intruder’s DHCP reply offers an IP address and supporting information that designates the intruder as the default gateway or Domain Name System (DNS) server. In the case of a gateway, the clients will then forward packets to the attacking device, which will in turn send them to the desired destination. This is referred to as a “man-in-the-middle” attack, and it may go entirely undetected as the intruder intercepts the data flow through the network.
Untrusted ports are those that are not explicitly configured as trusted. A DHCP binding table is built for untrusted ports. Each entry contains the client MAC address, IP address, lease time, binding type, VLAN number, and port ID recorded as clients make DHCP requests. The table is then used to filter subsequent DHCP traffic. From a DHCP snooping perspective, untrusted access ports should not send any DHCP server responses, such as DHCPOFFER, DHCPACK, DHCPNAK.