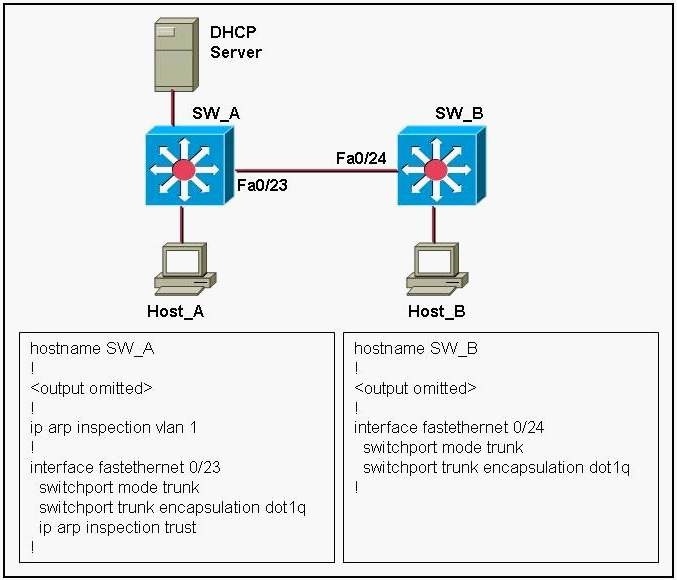
Refer to the exhibit. Dynamic ARP inspection (DAI) is enabled on switch SW_A only. Both Host_A and Host_B acquire their IP addresses from the DHCP server connected to switch SW_A. What would the outcome be if Host_B initiated an ARP spoof attack toward Host_A?

A.
The spoof packets will be inspected at the ingress port of switch SW_A and will be permitted.
B.
The spoof packets will not be inspected at the ingress port of switch SW_A and will be permitted.
C.
The spoof packets will not be inspected at the ingress port of switch SW_A and will be dropped.
D.
The spoof packets will be inspected at the ingress port of switch SW_A and will be dropped.
Explanation:
When configuring DAI, follow these guidelines and restrictions:
DAI is an ingress security feature; it does not perform any egress checking. DAI is not effective for hosts connected to routers that do not support DAI or that do not have this feature enabled. Because man-in-the-middle attacks are limited to a single Layer 2 broadcast domain, separate the domain with DAI checks from the one with no checking. This action secures the ARP caches of hosts in the domain enabled for DAI.
DAI depends on the entries in the DHCP snooping binding database to verify IP-to-MAC address bindings in incoming ARP requests and ARP responses. Make sure to enable DHCP snooping to permit ARP packets that have dynamically assigned IP addresses. When DHCP snooping is disabled or in non-DHCP environments, use ARP ACLs to permit or to deny packets.
DAI is supported on access ports, trunk ports, EtherChannel ports, and private VLAN ports.
In our example, since SW_B does not have DAI enabled (bullet point 2 above) packets will not be inspected and they will be permitted.
Reference:
http://www.cisco.com/en/US/docs/routers/7600/ios/12.2SXF/configuration/guide/dynarp.html