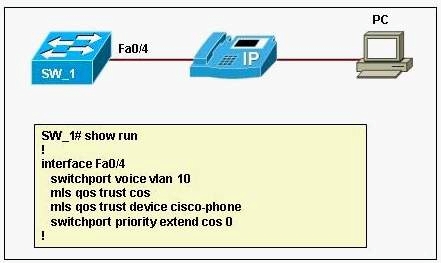
A workstation PC is connected to the Cisco IP phone access port.
Based on the configuration in the exhibit, how will the traffic be managed?

A.
The IP phone access port will override the priority of the frames received from the PC.
B.
The switch port Fa0/4 will trust the priority for the frames received from the PC.
C.
The IP phone access port will trust the priority of the frames received from the PC.
D.
The switch port Fa0/4 will override the priority of the frames received from the PC.
Explanation:
When a Cisco IP Phone is connected to a switch port, think of the phone as another switch
(which it is). If you install the phone as a part of your network, you can probably trust the
QoS information relayed by the phone.
However, remember that the phone also has two sources of data:
The VoIP packets native to the phone—The phone can control precisely what QoS
information is included in the voice packets because it produces those packets.
The user PC data switch port—Packets from the PC data port are generated elsewhere, so
the QoS information can not necessarily be trusted to be correct or fair.
A switch instructs an attached IP Phone through CDP messages as to how it should extend
QoS trust to its own user data switch port. To configure the trust extension, use the following
interface configuration command:
Switch(config-if)# switchport priority extend {cos value | trust}
Normally, the QoS information from a PC connected to an IP Phone should not be trusted.
This is because the PC’s applications might try to spoof CoS or Differentiated Services Code
Point (DSCP) settings to gain premium network service. In this case, use the cos keyword so
that the CoS bits are overwritten to value by the IP Phone as packets are forwarded to the
switch. If CoS values from the PC cannot be trusted, they should be overwritten to a value of
0.
In some cases, the PC might be running trusted applications that are allowed to request
specific QoS or levels of service. Here, the IP Phone can extend complete QoS trust to the
PC, allowing the CoS bits to be forwarded through the phone unmodified. This is done with
the trust keyword.