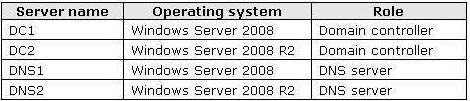
Your network contains an Active Directory domain named contoso.com. The domain
contains the servers shown in the following table.
The functional level of the forest is Windows Server 2003. The functional level of the domain
is Windows Server 2003.
DNS1 and DNS2 host the contoso.com zone.
All client computers run Windows 7 Enterprise.
You need to ensure that all of the names in the contoso.com zone are secured by using
DNSSEC.
What should you do first?

A.
Change the functional level of the forest.
B.
Change the functional level of the domain.
C.
Upgrade DC1 to Windows Server 2008 R2.
D.
Upgrade DNS1 to Windows Server 2008 R2.
Explanation:
http://technet.microsoft.com/en-us/library/ee683904%28v=ws.10%29.aspx
DNS Security Extensions (DNSSEC)
What are the major changes?
Support for Domain Name System Security Extensions (DNSSEC) is introduced in Windows
Server® 2008 R2 and Windows® 7. With Windows Server 2008 R2 DNS server, you can
now sign and host DNSSECsigned zones to provide security for your DNS infrastructure.
The following changes are available in DNS server in Windows Server 2008 R2:
Ability to sign a zone and host signed zones.
Support for changes to the DNSSEC protocol.
Support for DNSKEY, RRSIG, NSEC, and DS resource records.
The following changes are available in DNS client in Windows 7:
Ability to indicate knowledge of DNSSEC in queries.
Ability to process the DNSKEY, RRSIG, NSEC, and DS resource records.
Ability to check whether the DNS server with which it communicated has performed
validation on the client’s behalf.
The DNS client’s behavior with respect to DNSSEC is controlled through the Name
Resolution Policy Table (NRPT), which stores settings that define the DNS client’s behavior.
The NRPT is typically managed through Group Policy.What does DNSSEC do?
DNSSEC is a suite of extensions that add security to the DNS protocol. The core DNSSEC
extensions are specified in RFCs 4033, 4034, and 4035 and add origin authority, data
integrity, and authenticated denial of existence to DNS. In addition to several new concepts
and operations for both the DNS server and the DNS client, DNSSEC introduces four new
resource records (DNSKEY, RRSIG, NSEC, and DS) to DNS.
In short, DNSSEC allows for a DNS zone and all the records in the zone to be
cryptographically signed.
When a DNS server hosting a signed zone receives a query, it returns the digital signatures
in addition to the records queried for. A resolver or another server can obtain the public key
of the public/private key pair and validate that the responses are authentic and have not
been tampered with. In order to do so, the resolver or server must be configured with a trust
anchor for the signed zone, or for a parent of the signed zone.