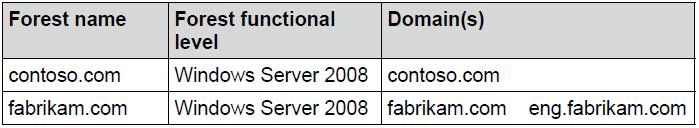
Your company has two Active Directory forests as shown in the following table.
The forests are connected by using a two-way forest trust. Each trust direction is configured
with forest-wide authentication. The new security policy of the company prohibits users from
the eng.fabrikam.com domain to access resources in the contoso.com domain.
You need to configure the forest trust to meet the new security policy requirement.
What should you do?

A.
Delete the outgoing forest trust in the contoso.com domain.
B.
Delete the incoming forest trust in the contoso.com domain.
C.
Change the properties of the existing incoming forest trust in the contoso.com domain
from Forest-wide authentication to Selective authentication.
D.
Change the properties of the existing outgoing forest trust in the contoso.com domain to
exclude *.eng. fabrikam.com from the Name Suffix Routing trust properties.
Explanation:
http://technet.microsoft.com/en-us/library/cc773178%28v=ws.10%29.aspx
How Domain and Forest Trusts Work
Active Directory provides security across multiple domains or forests through domain and
forest trust relationships. Before authentication can occur across trusts, Windows must first
determine whether the domain being requested by a user, computer or service has a trust
relationship with the logon domain of the requesting account. To make this determination,
the Windows security system computes a trust path between the domain controller for the
server that receives the request and a domain controller in the domain of the requesting
account.
..
Trust Flow
The flow of secured communications over trusts determines the elasticity of a trust: how you
create or configure a trust determines how far the communication extends within a forest or
across forests. The flow of communication over trusts is determined by the direction of the
trust (one-way or two-way) and the transitivity of the trust (transitive or nontransitive).
One-Way and Two-Way Trusts
Trust relationships that are established to enable access to resources can be either one-way
or two-way. A one-way trust is a unidirectional authentication path created between two
domains. In a one-way trust between Domain A and Domain B, users in Domain A can
access resources in Domain B. However, users in Domain B cannot access resources in
Domain A. Some one-way trusts can be either nontransitive or transitive depending on the
type of trust being created.
All domain trusts in an Active Directory forest are two-way, transitive trusts. When a new
child domain is created, a two-way, transitive trust is automatically created between the new
child domain and the parent domain. In a two-way trust, Domain A trusts Domain B and
Domain B trusts Domain A. This means that authentication requests can be passed between
the two domains in both directions. Some two-way relationships can be nontransitive or
transitive depending on the type of trust being created. An Active Directory domain can
establish a one-way or two-way trust with:
Windows Server 2003 domains in the same forest.
Windows Server 2003 domains in a different forest.
Windows NT 4.0 domains.
Kerberos V5 realms.
Transitive and Nontransitive Trusts
Transitivity determines whether a trust can be extended outside of the two domains with
which it was formed. A transitive trust can be used to extend trust relationships with other
domains; a nontransitive trust can be used to deny trust relationships with other domains.
Each time you create a new domain in a forest, a two-way, transitive trust relationship is
automatically created between the new domain and its parent domain. If child domains are
added to the new domain, the trust path flows upward through the domain hierarchyextending the initial trust path created between the new domain and its parent domain.
Transitive trust relationships flow upward through a domain tree as it is formed, creating
transitive trusts between all domains in the domain tree.
Authentication requests follow these trust paths, so accounts from any domain in the forest
can be authenticated by any other domain in the forest. With a single logon process,
accounts with the proper permissions can access resources in any domain in the forest. The
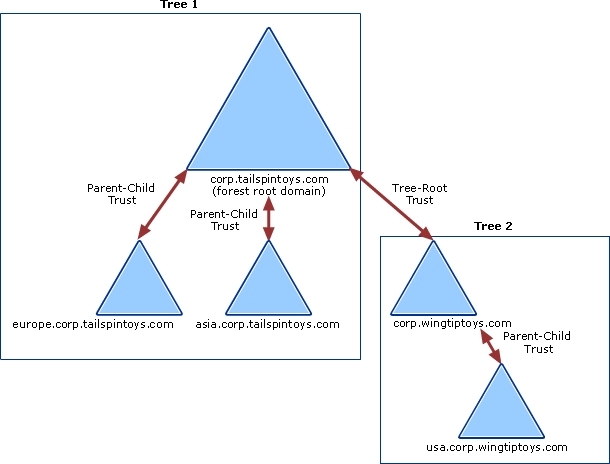
following figure shows that all domains in Tree 1 and Tree 2 have transitive trust
relationships by default. As a result, users in Tree 1 can access resources in domains in
Tree 2 and users in Tree 1 can access resources in Tree 2, when the proper permissions
are assigned at the resource.
Default Transitive Trust RelationshipsIn addition to the default transitive trusts established in a Windows Server 2003 forest, by
using the New Trust Wizard you can manually create the following transitive trusts.
Shortcut trust. A transitive trust between domains in the same domain tree or forest that is
used to shorten the trust path in a large and complex domain tree or forest.
Forest trust. A transitive trust between one forest root domain and another forest root
domain.
Realm trust. A transitive trust between an Active Directory domain and a Kerberos V5 realm.
A nontransitive trust is restricted to the two domains in the trust relationship and does not
flow to any other domains in the forest. A nontransitive trust can be a two-way trust or a oneway trust.
Nontransitive trusts are one-way by default, although you can also create a two-way
relationship by creating two one-way trusts. Nontransitive domain trusts are the only form of
trust relationship possible between:A Windows Server 2003 domain and a Windows NT domain
A Windows Server 2003 domain in one forest and a domain in another forest (when not
joined by a forest trust)
By using the New Trust Wizard, you can manually create the following nontransitive trusts:
External trust. A nontransitive trust created between a Windows Server 2003 domain and a
Windows
NT, Windows 2000, or Windows Server 2003 domain in another forest. When you upgrade a
Windows NT domain to a Windows Server 2003 domain, all existing Windows NT trusts are
preserved intact. All trust relationships between Windows Server 2003 domains and
Windows NT domains are nontransitive.
Realm trust
A nontransitive trust between an Active Directory domain and a Kerberos V5 realm