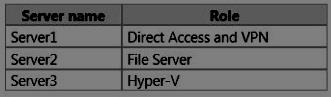
Your network contains an Active Directory domain named contoso.com. The domain contains three
servers. The servers are configured as shown in the following table.
You need to ensure that end-to-end encryption is used between clients and Server2 when the clients
connect to the network by using DirectAccess.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose
two.)

A.
From the Remote Access Management Console, reload the configuration.
B.
Add Server2 to a security group in Active Directory.
C.
Restart the IPSec Policy Agent service on Server2.
D.
From the Remote Access Management Console, modify the Infrastructure Servers settings.
E.
From the Remote Access Management Console, modify the Application Servers settings.
Explanation:
Unsure about these answers:
A public key infrastructure must be deployed.
Windows Firewall must be enabled on all
profiles.
ISATAP in the corporate network is not
supported. If you are using ISATAP, you should remove
it and use native IPv6.
Computers that are running the following
operating systems are supported as DirectAccess
clients:
Windows Server® 2012 R2
Windows 8.1 Enterprise
Windows Server® 2012
Windows 8 Enterprise
Windows Server® 2008 R2
Windows 7 Ultimate
Windows 7 Enterprise
Force tunnel configuration is not supported
with KerbProxy authentication.
Changing policies by using a feature other than
the DirectAccess management console or Windows
PowerShell cmdlets is not supported.
Separating NAT64/DNS64 and IPHTTPS server
roles on another server is not supported.


https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/jj134239(v=ws.11)
2.6. Configure application servers
In a Remote Access deployment, configuring application servers is an optional task. Remote Access enables you to require authentication for selected application servers, which is determined by their inclusion in an application servers security group. By default, traffic to application servers that require authentication is also encrypted; however, you can choose to not encrypt traffic to application servers and use authentication only.
0
0