###BeginCaseStudy###
Topic 3: Northwind Traders
No. of Questions: 10
Overview
Northwind Traders is an IT services and hosting provider.
Northwind Traders has two main data centers in North America. The data centers are located in the same city. The data centers
connect to each other by using high-bandwidth, low-latency WAN links. Each data center connects directly to the Internet.
Northwind Traders also has a remote office in Asia that connects to both of the North American data centers by using a WAN link. The
Asian office has 30 multipurpose servers.
Each North American data center contains two separate network segments. One network segment is used to host the internal servers
of Northwind Traders. The other network segment is used for the hosted customer environments.
Existing Enviornment
Active Directory:
The network contains an Active Directory forest named northwindtraders.com. The forest contains a single domain. All servers run
Windows Server 2012 R2.
Server Enviornment:
The network has the following technologies deployed:
Service Provider Foundation
Windows Azure Pack for Windows Server
System Center 2012 R2 Virtual Machine Manager (VMM)
An Active Directory Rights Management Services (AD RMS) cluster
An Active Directory Certificate Services (AD CS) enterprise certification authority (CA)
All newly deployed servers will include the following components:
Dual 10-GbE Remote Direct Memory Access (RDMA)-capable network adapters
Dual 1-GbE network adapters
128 GB of RAM
Requirments
Business Goals:
Northwind Traders will provide hosting services to two customers named Customer1 andCustomer2.
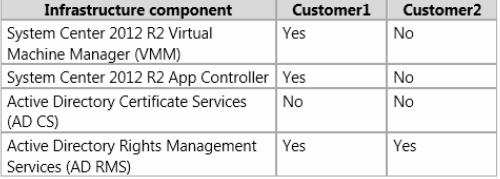
The network of each customer is configured as shown in the following table.
Planned Changes:
Northwind Traders plans to implement the following changes:
Deploy System Center 2012 R2 Operations Manager.
Deploy Windows Server 2012 R2 iSCSI and SMB-based storage.
Implement Hyper-V Recovery Manager to protect virtual machines.
Deploy a certificate revocation list (CRL) distribution point (CDP) on the internal network.
For Customer 1, install server authentication certificates issued by the CA of Northwind Traders on the virtual machine in the hosting
networks.
General Requirements:
Northwind Traders identifies the following requirements:
Storage traffic must use dedicated adapters.
All storage and network traffic must be load balanced.
The amount of network traffic between the internal network and the hosting network must be minimized.
The publication of CRLs to CDPs must be automatic.
Each customer must use dedicated Hyper-V hosts.
Administrative effort must be minimized, whenever possible.
All servers and networks must be monitored by using Operations Manager.
Anonymous access to internal file shares from the hosting network must be prohibited.
All Hyper-V hosts must use Cluster Shared Volume (CSV) shared storage to host virtual machines.
All Hyper-V storage and network traffic must remain available if single network adapter fails.
The Hyper-V hosts connected to the SMB-based storage must be able to make use of the RDMA technology.
The number of servers and ports in the hosting environment to which the customer has access must be minimized.
Customer1 Requirements:
Northwind Traders identifies the following requirements for Customer1:
Customer1 must use SMB-based storage exclusively.
Customer1 must use App Controller to manage hosted virtual machines.
The virtual machines of Customer1 must be recoverable if a single data center fails.
Customer1 must be able to delegate self-service roles in its hosted environment to its users.
Customer1 must be able to check for the revocation of certificates issued by the CA of Northwind Traders.
The users of Customer1 must be able to obtain use licenses for documents protected by the AD RMS of Northwind Traders.
Certificates issued to the virtual machines of Customer1 that reside on the hosted networks must be renewed automatically.
Customer2 Requirements:
Northwind Traders identifies the following requirements for Customer2:
Customer2 must use iSCSI-based storage exclusively.
All of the virtual machines of Customer2 must be migrated by using a SAN transfer.
None of the metadata from the virtual machines of Customer2 must be stored in Windows Azure.
The network configuration of the Hyper-V hosts for Customer2 must be controlled by using logical switches.
The only VMM network port profiles and classifications allowed by Customer2 must be low-bandwidth, medium-bandwidth, or highbandwidth.
The users at Northwind Traders must be able to obtain use licenses for documents protected by the AD RMS cluster of Customer2.
Customer2 plans to decommission its AD RMS cluster during the next year.
###EndCaseStudy###
You need to recommend a monitoring solution for Northwind Traders.
What is the best approach to achieve the goal? More than one answer choice may achieve the goal. Select the BEST answer.

A.
Three Operations Manager management servers and two Operations Manager gateway servers
B.
One Operations Manager management server
C.
Two Operations Manager management servers and three Operations Manager gateway servers
D.
Five Operations Manager management servers
Explanation:
In the section General requirements states that
All servers and networks must be monitored by System Center 2012 R2 Operations Manager.System Center 2012 – Operations Manager requires mutual authentication be performed between agents and management servers prior to the exchange of
information between them. To secure the authentication process between the two, the process is encrypted. When the agent and the management server reside in
the same Active Directory domain or in Active Directory domains that have established trust relationships, they make use of Kerberos V5 authentication
mechanisms provided by Active Directory. When the agents and management servers do not lie within the same trust boundary, other mechanisms must be used to
satisfy the secure mutual authentication requirement.
In Operations Manager, this is accomplished through the use of X.509 certificates issued for each computer. If there are many agent-monitored computers, this
results in high administrative overhead for managing all those certificates. In addition, if there is a firewall between the agents and management servers, multiple
authorized endpoints must be defined and maintained in the firewall rules to allow communication between them.
To reduce this administrative overhead, Operations Manager has a server role called the gateway server. Gateway servers are located within the trust boundary of
the agents and can participate in the mandatory mutual authentication. Because they lie within the same trust boundary as the agents, the Kerberos V5 protocol for
Active Directory is used between the agents and the gateway server. Each agent then communicates only with the gateway servers that it is aware of. The gateway
servers communicate with the management servers.To support the mandatory secure mutual authentication between the gateway servers and the management servers, certificates must be issued and installed, but
only for the gateway and management servers. This reduces the number of certificates required, and in the case of an intervening firewall it also reduces the
number of authorized endpoints to be defined in the firewall rules. The following illustration shows the authentication relationships in a management group using a
gateway server.
https://technet.microsoft.com/en-us/library/hh212823.aspx


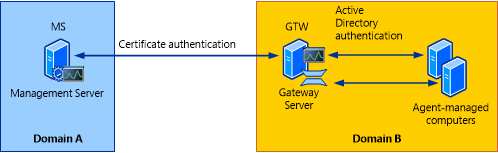
Operations Manager management server at each main DC
Operations Manager gateway server at remote office in Asia, Customer 1 and Customer 2
0
0