Which of the following uses the same key to decrypt as it does to encrypt?

A.
Certificate-based encryption
B.
Static encryption
C.
Asymmetric encryption
D.
Dynamic encryption
E.
Symmetric encryption
Explanation:
Symmetric Encryption
Symmetric encryption
is best described graphically, as shown in Figure below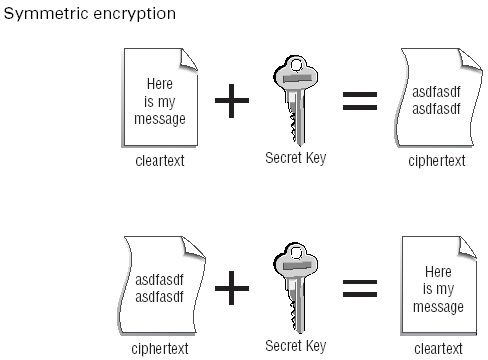
The original message shown in Figure 6.1 is referred to as being in
cleartext
because it’s readable. When this original message is combined with the secret
key the result is the encrypted message (referred to as
ciphertext
). The message
can only be decrypted by someone who holds the same secret key. When the
process is reversed, the encrypted message together with the secret key will
produce the original cleartext message.
The process is relatively simple and very quick, but it has some drawbacks;
the most basic is that the same key used to encrypt is also used to
decrypt. The secret key must be created and then securely delivered to the
person with whom you want to share encrypted messages. The safest way is
to put it on a floppy disk and physically carry it to the person, but it is not
always possible to do so. It’s not secure to send this key via e-mail, because
anyone could intercept it and read all of your encrypted messages. Even if
you’re able to physically get the key to the person, it is good security practice
to change the key on a regular basis. When you’re exchanging messages with
one person, this is not a big deal-but with multiple people, it would be a
daunting task. With symmetric encryption you should have a separate key
for each person with whom you want to share encrypted information. If you
used the same key for everyone, then everyone would be able to read all the
messages sent. So you need to generate one key for every person with whom
you wish to encrypt. As the number of keys grows, key management
becomes an issue.We’re not saying that symmetric encryption doesn’t have a place in a
VPN. However, you’ll have to address the problem of key management. This
leads us to asymmetric encryption


