Which of the following FTP Content Security settings prevents internal users from sending
corporate files to external FTP Servers, while allowing users to retrieve files?

A.
Use an FTP resource, and enable the GET and PUT methods.
B.
Use an FTP resource and enable the GET method.
C.
Use an FTP resource and enable the PUT method.
D.
Block FTP_PASV.
E.
Block all FTP traffic.
Explanation:
FTP
The FTP (File Transfer Protocol) SmartDefense group essentially has two
purposes: It can protect your system against a specific FTP attack called FTP
Bounce, and it lets you configure your FTP Security Server.
FTP Bounce
The FTP Bounce attack takes advantage of a design flaw in FTP. Port 20 is
where the FTP PORT command negotiates a random high port for PASV
transport of FTP data files. RFC 959, which describes FTP, dictates that the
negotiated high port be allowed to any IP address and any port. The FTP
Bounce attack takes advantage of this and the attacker can open a connection
to a machine of their choosing for illegitimate purposes. You can select
the Track option for notification if a FTP Bounce attack is detected.
FTP Security Server
The firewall FTP Security Server provides authentication and content security
services (see Chapter 4,”Content Security,” for more details on the FTP
Security Server). Usually the FTP Security Server (showing below) is
invoked by rules in your rule base that specify an FTP Resource or User
Authentication. Selecting the Configurations Apply To All Connections radio
button forces all FTP connections through the FTP Security Server regardless
of whether your rule base contains an authentication or resource rule.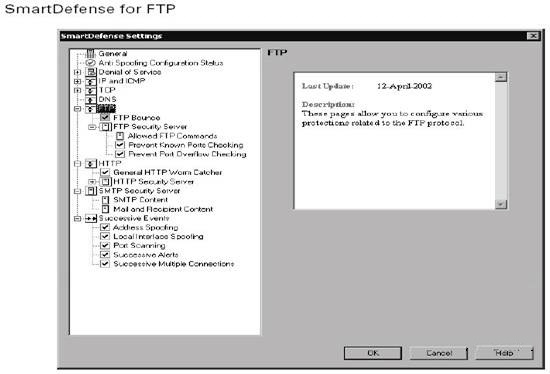
Selecting the default option of Configurations Apply Only To Connections
Related To Resources Used In The Rule Base will cause the FTP Security Server
to be invoked only when a resource or authentication rule in the rule base
triggers it.
You need to take into consideration three further settings when setting up
the FTP Security Server: Allowed FTP Commands, Prevent Known Port
Checking, and Prevent Port Overflow Checking:
Allowed FTP Commands The Allowed FTP Commands option, illustrated
in Figure below, gives you granular control over the FTP commands
the FTP Security Server will respond to. You can set Acceptable commands
and Blocked commands.
Prevent Known Port Checking The Prevent Known Port Checking
option allows you to specify whether you want the FTP Security Server to
allow connections to well-known ports. This option also provides another
line of defense against the FTP Bounce attack by not allowing a connection
to a well-known port.
Prevent Port Overflow Checking Prevent Port Overflow Checking is
another component to help prevent the FTP Bounce Attack. Turning on
this option turns off the checks that prevent numerous instances of connections
from/to the same port.




