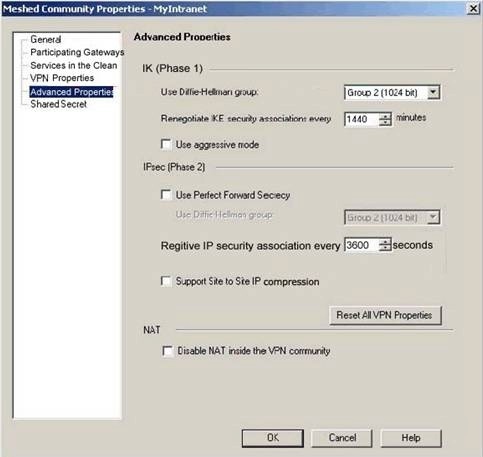
Dr Bill is senior Security Administrator who supervises and trains junior Security Administrators. Dr
Billmust explain VPN-1/FireWall-1’s Diffie-Hellman settings to the junior Security Administrator.
Which of the following explanations is MOST correct?

A.
Diffie-Hellman key settings are in the Advanced Properties for a reason. Incorrect DiffieHellman key settings can stop and Enforcement Module from passing any traffic at all. Incorrect
Diffie-Hellman key settings usually require a complete reinstallation.
B.
Diffie-Hellman groups exist for backward compatibility. When establishing VPN tunnels between
BG with Application Intelligence and older versions of VPN-1/FireWall-1, Diffie-Hellman groups
allow Security Administrators to accommodate older encryption algorithms.
C.
Diffie-Hellman key exchange is an encryption algorithm, which transforms clear text into
ciphertext. Diffie-Hellman is vulnerable to man-in-the-middle attacks. Diffie-Hellman groups with
higher numbers use stronger keys, but have no impact on performance.
D.
Diffie-Hellman key exchange is a cryptographic protocol, which allows two communicators to
agree on a secret key over an insecure communication channel. Diffie-Hellman groups with higher
numbers use stronger keys. But have a negative impact on performance.
E.
Diffie-Hellman keys are applied only when established Check Point-to-other-vendor VPNs.
When creating VPN tunnels between different vendor’s software, Diffie-Hellman keys
automatically negotiate IKE and IPSEC parameters.
Explanation:
Diffie-Hellman Key Exchange Mechanism
The
Diffie-Hellman
key exchange uses the public/private key pair to generate
a secret key. This process is illustrated in Figure below.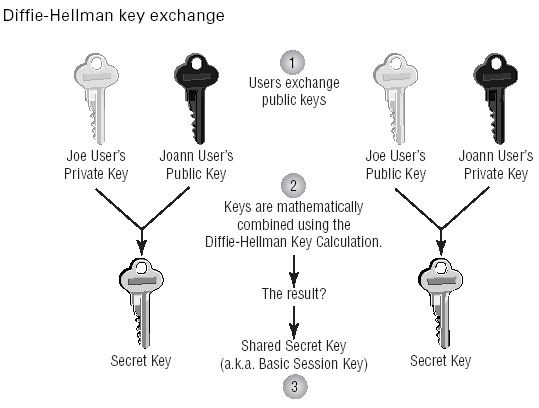
In step 1, users exchange public keys. When you’re using asymmetric
encryption, the exchange of public keys is all that is required to begin
encrypting. But Diffie-Hellman combines asymmetric and symmetric processes.
Each user’s private key is combined with their encrypting partners’
public key using the Diffie-Hellman key calculation, as shown in step 2. As
we stated earlier, the public and private keys that each user creates are mathematically
related; that’s how the users can exchange keys, apply the DiffieHellman key calculation, and both end up (in step 3) with mathematically
identical keys.
Different mathematical groups can be used to generate the identical keys. TheDiffie-Hellman standard supports three groups: DH groups 1, 2, and 5. The
larger the group number, the larger the prime number used to generate the
key pair. The larger groups are more secure but require more CPU cycles to
generate the keys. Check Point also gives you the ability to expand the database
of groups by adding custom groups.
The process depicted in Figure above solves two problems. First, you have
generated the secret key necessary to perform symmetric encryption without
having to physically exchange the secret key with your encrypting partner.
Second, you can use that key to symmetrically encrypt data much more
quickly than you can using asymmetric encryption alone. The best aspects of
both encryption techniques are combined to yield a process that’s better than
each individual technique.The encryption processes we’ve described fill out
the P in PAIN, but they are useless unless you get the correct key from your
encrypting partner. The next section addresses how to verify that the key is
from the correct source and explains the AIN in PAIN