HOTSPOT
You have an Exchange Server 2013 organization that contains a server named EX1.
The network contains two domain controllers named DC1 and DC2.
You plan to make changes to the Active Directory infrastructure and to remove DC2 from the
network.
You need to verify whether EX1 writes Active Directory changes to DC2.
What command should you run? To answer, select the appropriate options in the answer area.

Answer: See the explanation
Explanation:
Box 1: Get-OrganizationConfig
Box 2: DC2


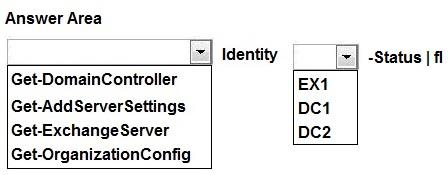
This should be Get-ExchangeServer -Identity EX1 -Status | FL? You can see the server’s current domain controller and GC in the output of that command.
0
0
It’s Get-ExchangeServer -Identity EX1 -Status | FL will list current DC and GC other command with OrgConfig will not work
0
0
Get-ExchangeServer -Identity EX1 -Status | FL looks right.
You can get-organizationconfig and then specify a DC
0
0
*can’t
0
0
220 is C
222 is A
0
0
Agreed with potpal and Joe. You’re basically looking to see if EX1 has DC2 set as a static domain controller.
0
0
The Get-OrganizationConfig cmdlet is used to get configuration data for an Exchange organization.
We should specify DC2 as we are interested if information from EX1 is propagated to DC2.
Example: This example gets the organization configuration information for the domain controller ContosoDC.
Get-OrganizationConfig -DomainController ContosoDC
Incorrect answers:
Not Get-ExchangeServer: The Get-ExchangeServer cmdlet is used to obtain the attributes of a specified Exchange server, but we are not interested in the attributes of EX1, we want to know if EX1 propagates changes to DC2.
Not Get-DomainController: The Get-DomainController cmdlet is used to view a list of domain controllers that exist in your organization, but we are interested in Active Directory information not a list of the Domain controllers.
Not Get-AddServerSettings: The Get-AdServerSettings cmdlet is used to view the Active Directory Domain Services (AD DS) environment settings in the current Windows PowerShell session, but we are not interested in PowerShell sessions.
https://technet.microsoft.com/en-us/library/aa997571%28v=exchg.150%29.aspx
0
0
As per given options>>> Get-OrganizationConfig Identity DC2″ will return “A positional parameter cannot be found that accepts argument ‘DC2′”.
According
https://technet.microsoft.com/en-us/library/aa997571(v=exchg.150)
Identity expects “The Identity parameter specifies the organization you want configuration data from.”
So I will agree with Potpal and Joe!
0
0
Get-ExchangeServer:
The DomainController parameter specifies the domain controller that’s used by this cmdlet to read data from or write data to Active Directory. You identify the domain controller by its fully qualified domain name (FQDN). For example, dc01.contoso.com.
Get-OrganizationConfig:
The DomainController parameter specifies the fully qualified domain name (FQDN) of the domain controller that retrieves data from Active Directory.
Question: You need to verify whether EX1 writes Active Directory changes to DC2.
So you have to determine if one specific Exchange server communicates with one specific DC. I would go with Get-ExchangeServer.
0
0
better explanation:
Get-OrganizationConfig – checks if EX reads data from DC
Get-ExchangeServer – checks if EX reads from OR writes data to DC
Question: You need to verify whether EX1 writes Active Directory changes to DC2.
Correct answer is Get-ExchangeServer, becasue we want to know if EX1 writes data to DC2
0
0
New 70-341 Exam Questions and Answers Updated Recently (15/Aug/2016):
NEW QUESTION 243
You have an Exchange Server 2013 organization that contains the servers configured as shown in the following table.
Image URL: examgod.com/plimages/109f6fbf8b00_C7D6/70-341-vce-pdf-dumps-2431_thumb.jpg
All inbound messages from the Internet are received by EX1 and EX2. You notice several communication errors between Subnet1 and Subnet2. Another administrator is working to resolve the communication errors. You need to identify if email delivery to the organization fails due to the communication errors by monitoring the inbound TCP ports in Subnet2. Which port should you monitor?
A. 25
B. 475
C. 587
D. 2525
Answer: A
NEW QUESTION 244
You have an Exchange Server 2013 organization that contains five servers. The organization contains 5,000 mailboxes. One hundred users plan to leave your company during the next 48 hours to run a new company named Fabrikam, Inc. The mailboxes of the 100 users are in a mailbox database named DB5. The deleted item retention setting for DB5 is two days. You need to implement a solution to meet the following security requirements:
– The 100 users must be prevented from permanently deleting any email messages from their mailbox.
– In 48 hours, you must create a copy of only the email messages that contain the word “Fabrikam”.
– The solution must be implemented as quickly as possible.
What should you do?
A. Modify the deleted item retention period for DB5, and then run the New-MailboxSearch cmdlet in 48 hours.
B. Modify the deleted item retention period for the 100 mailboxes, and then run the New-MailboxSearch cmdlet in 48 hours.
C. Modify the deleted item retention period for DB5, and then run the Search-Mailbox cmdlet in 48 hours.
D. Enable Single Item Recovery for the 100 mailboxes, and then run the New-MailboxSearch cmdlet in 48 hours.
Answer: C
Explanation:
Not A. New-MailboxSearch alone will just create a search.
You would need to run the Start-MailboxSearch cmdlet to actually run the search.
technet.microsoft.com/en-us/library/ee364752(v=exchg.150).aspx
technet.microsoft.com/en-us/library/dd298173(v=exchg.160).aspx
NEW QUESTION 245
Hotspot Question
You have an Exchange Server 2013 organization and a Microsoft Office 365 tenant that are configured for hybrid coexistence. Fight hundred users have mailboxes in the Exchange Server 2013 organization. Six hundred users have mailboxes in Office 365. You need to implement a mailbox solution for the support department. The solution must meet the following reguirements:
– All users must be able to send email messages to a dedicated mailbox for support.
– All of the users from the support department must be able to log on to the dedicated support mailbox and read the email messages in the mailbox.
– All of the users from the support department must be able to reply to the email messages sent to the dedicated support mailbox. The replies must identify to the name of the user replying.
– Must apply the principle of least privileges.
What should you do? To answer, select the appropriate options in the answer area.
Image URL: examgod.com/plimages/109f6fbf8b00_C7D6/70-341-vce-pdf-dumps-2451_thumb.jpg
Answer:
Image URL: examgod.com/plimages/109f6fbf8b00_C7D6/70-341-vce-pdf-dumps-2452_thumb.png
NEW QUESTION 246
You plan lo deploy three Exchange Server 2013 servers. Each server has eight 1-TB internal hard disk drives for mailbox database storage. All of the mailbox databases will replicate to all of the servers. You need to recommend a disk configuration for the servers that meets the following reguirements:
– Users must be able to access their mailbox if a single disk fails.
– The amount of space available for mailbox data must be maximized.
Which disk configuration should you use on each server?
A. JBOD
B. RAID 5
C. RAID 1
D. RAID 10
Answer: B
NEW QUESTION 247
Your network contains an Active Directory forest named contoso.com. The forest contains four sites named Site 1, Site2, Site3, and Site4. You have an Exchange Server 2013 organization that contains several servers in each site. You need to prevent users who have mailboxes in Site2 from sending email messages that are larger than 2 MB to recipients in Site3. What should you do?
A. Run the Set-ADSiteLink cmdlet.
B. Create a message classification.
C. Create a custom Send connector.
D. Run the Set-ADSite cmdlet.
Answer: A
Explanation:
technet.microsoft.com/en-us/library/bb123696(v=exchg.141).aspx
NEW QUESTION 248
Hotspot Question
You have an Exchange Server 2013 organization. All users connect to their mailbox by using a mobile device. You need to ensure that an event is written to the application log when a user attempts to connect to the organization by using a second mobile device. What command should you run? To answer, select the appropriate options in the answer area.
Image URL: examgod.com/plimages/109f6fbf8b00_C7D6/70-341-vce-pdf-dumps-2481_thumb.jpg
Answer:
Image URL: examgod.com/plimages/109f6fbf8b00_C7D6/70-341-vce-pdf-dumps-2482_thumb.jpg
Explanation:
technet.microsoft.com/en-us/library/dd298094(v=exchg.160).aspx
NEW QUESTION 249
Hotspot Question
You plan to deploy an Exchange Server 2013 organization. The security department identifies the following reguirements for the planned deployment:
– Only members of a security group named ExSecure must be able to create Exchange Server recipients.
– Only members of a security group named ExSecureAdmin must be able to manage Exchange Server organization configurations.
– Members of ExSecure and ExSecureAdmin must be able to use the Exchange Management Shell to manage Active Directory objects.
You need to identify which permission model must be used to meet each requirement. What should you identify? To answer, select the appropriate options in the answer area.
Image URL: examgod.com/plimages/109f6fbf8b00_C7D6/70-341-vce-pdf-dumps-2491_thumb.jpg
Answer:
Image URL: examgod.com/plimages/109f6fbf8b00_C7D6/70-341-vce-pdf-dumps-2492_thumb.png
Explanation:
technet.microsoft.com/en-us/library/dd638106(v=exchg.150).aspx
NEW QUESTION 250
Your company has five main offices. Each office contains a data center. You plan to deploy an Active Directory forest and an Exchange Server 2013 organization. Each office will be configured as a separate Active Directory site. User mailboxes will be hosted in each site. You need to recommend an Exchange Server 2013 deployment strategy that meets the following requirements:
– Provides redundancy for all mailbox databases
– Creates a temporary copy of outbound email messages
– Minimizes the number of servers deployed to the network
– Provides redundancy for client access by using Network Load Balancing (NLB)
What should you recommend?
A. In each site, deploy one server that has both the Mailbox server role and the Client Access server role installed and another server that has the Client Access server role installed.
B. In each site, deploy one server that has the Mailbox server role installed and two servers that have the Client Access server role installed.
C. In each site, deploy one server that has both the Mailbox server role and the Client Access server role installed.
D. In each site, deploy two servers that have both the Mailbox server role and the Client Access server role installed.
Answer: B
Explanation:
WNLB can’t be used on Exchange servers where mailbox DAGs are also being used because WNLB is incompatible with Windows failover clustering. If you’re using an Exchange 2013 DAG and you want to use WNLB, you need to have the Client Access server role and the Mailbox server role running on separate servers.
technet.microsoft.com/en-us/library/jj898588(v=exchg.150).aspx
NEW QUESTION 251
……
P.S. These New 70-341 Exam Questions Were Just Updated From The Real 70-341 Exam, You Can Get The Newest 70-341 Dumps In PDF And VCE From — https://tr.im/1banM (261q)
Good Luck !!!
0
0
BTW, NEW 70-341 PDF Dumps from Google Drive for Free: https://tr.im/1vD8Y
0
0
Superb site you have here but I was curious if you knew of any user discussion forums that cover the same topics talked about here? I’d really love to be a part of community where I can get feed-back from other experienced people that share the same interest. If you have any suggestions, please let me know. Bless you!|
0
0
Hello!!!!
What should be the answers in the new question 221????
0
0