HOTSPOT
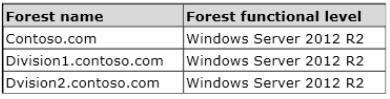
Your network contains three Active Directory forests. The forests are configured as shown in the
following table.
A two-way forest trust exists between contoso.com and divisionl.contoso.com. A two-way forest
trust also exists between contoso.com and division2.contoso.com.
You plan to create a one-way forest trust from divisionl.contoso.com to division2.contoso.com.
You need to ensure that any cross-forest authentication requests are sent to the domain controllers
in the appropriate forest after the trust is created.
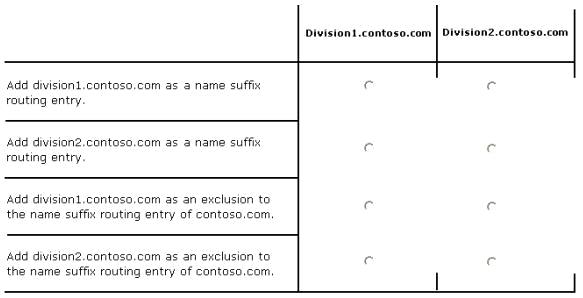
How should you configure the existing forest trust settings?
In the table below, identify which configuration must be performed in each forest. Make only one
selection in each column. Each correct selection is worth one point.

Explanation:
There will be a one-way forest trust from division1.contoso.com to division2.contoso.com
Division1 trusts Division2. Division2 must be able to access resources in Division1.Division1 should not be able to access resources in Division2.



https://blogs.technet.microsoft.com/askds/2009/04/10/name-suffix-routing/
1
0
Thanks Gion
that article your reference made the image clear for mean
Here is a quote form it:
“When a Forest Trust is created a Name Suffix Route is dynamically added to both sides of the Forest Trust Properties. The Name Suffix Route is comprised of the DNS name suffix of the trusted forest root and a wildcard (*) precedes the DNS name suffix to allow for child domains to be trusted implicitly. The name suffix looks like this: *.CONTOSO.COM.
Name Suffixes Routing controls routing of authentication traffic. When an account attempts to authenticate and that account does not exist in the local domain, the Name Suffix Route is used to direct authentication requests to the trusted forest root domain.”
To solve the problem:
“When more than two Forest reside in the same DNS namespace, and the root of that DNS tree is also an Active Directory forest, logic must be added to the Name Suffix Route to ensure authentication traffic is routed to the correct forest root. This can be accomplished by adding Exclusions to the Name Suffix Routes”
1
0
best explanation i have seen:
Sanan says:
March 6, 2016 at 12:03 pm
When an account (from the division2) attempts to authenticate (to the division1) and that account does not exist in the local domain (in the division1), the Name Suffix Route is used to direct authentication requests to the trusted forest root domain (to the division2)
0
0
OSA says:
September 17, 2015 at 5:12 am
Based on the following article “http://blogs.technet.com/b/askds/archive/2009/04/10/name-suffix-routing.aspx”, answer above may be wrong.
Answer is more likely to be :
1. Add division2.contoso.com as an exclusion to the name suffix routing entry of contoso.com on Division1.contoso.com ( as above)
2. Add division1.contoso.com as an exclusion to the name suffix routing entry of contoso.com on Division2.contoso.com
Reply
JohnnyDivin’Duck says:
October 18, 2015 at 4:16 am
Agreed.
Apparently even though the trust between divisions domains is configured one-way.
Still, we need to prevent authentication requests going from division1 to contoso.com forest.
0
0
These are three separate forests, even if the naming implies otherwise (Which is why there is a problem to begin with).
Between forests, all trusts need to be specifically implemented.
And according to MS, if you implement a trust, the routing is set for you.
The thing with this question is:
Even before you implement the one way trust, this setup has issues.
If you wanted to login from one division to another, you wouldn’t get a proper deny, but either would send the packet to contoso.com (because *div(x).cont.com routes to *.cont.com because of the two way trusts, assuming that div(x) is a child domain of contoso.com, which they aren’t)
So basically even without the one way trust it would be more proper to already exclude the two divs from routing.
Reply
0
0