Which of the following commands can be used to determine the SPI that a router will use to reach an active
IPSec peer? (Select the best answer.)

A.
show crypto ipsec sa
B.
show crypto session
C.
show crypto isakmp sa active
D.
show crypto ipsec securityassociation
Explanation:
The show crypto ipsec sa command can be used to determine the Security Parameter Index (SPI) that a router
will use to reach an active IP Security (IPSec) peer. Each IPSec security association (SA) is uniquely identified
by its corresponding IPSec peer address, security protocol, and SPI. Because IPSec SAs are unidirectional,
two SAs are required between active IPSec peers: an inbound SA and an outbound SA. The SPI associated
with the outbound SA is generated by the local peer during phase 2 of the Internet Key
Exchange (IKE) negotiation process and is used by the remote peer as the inbound SPI associated with this
SA. Likewise, the SPI associated with the inbound SA on the local peer corresponds to the outbound SPI that
was generated by the remote peer during its portion of phase 2 negotiations.
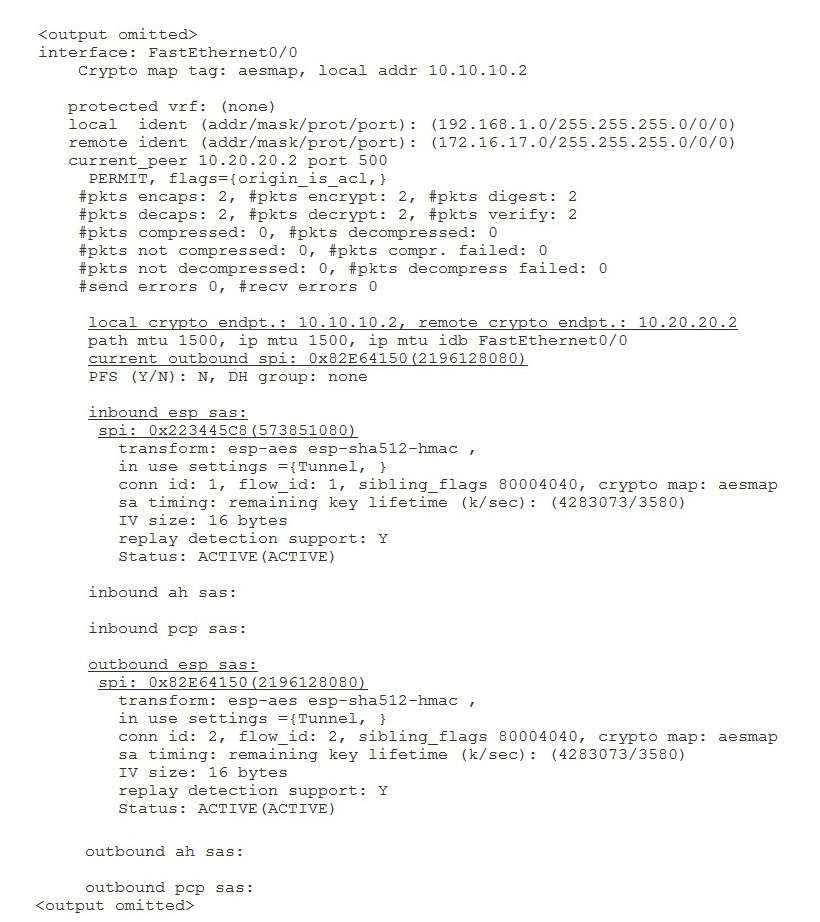
The show crypto ipsec sa command displays detailed information about IPSec SAs, including the IP addresses
of the crypto endpoints (IPSec peers), the number of packets encrypted and decrypted, the security protocol,
and the corresponding SPIs. For example, the following partial command output shows the SPIs associated
with the SAs between the local peer, 10.10.10.2, and the remote peer 10.20.20.2 on interface FastEthernet 0/0:The show crypto session command displays a summary of all current IKE SAs and their corresponding IPSec
SAs? however, the command does not display the SPI that a router will use to reach an active IPSec peer.
Sample output from the show crypto sessioncommand is shown below:The show crypto isakmp sa active command displays active IKE SAs, not configuration and operational details
of an IPSec connection. SA information is displayed in a summarized format, as shown below:
dst src state connid slot status
10.20.20.2 10.10.10.2 QM_IDLE 1 0 ACTIVE
For each SA, the dst field displays the IP address of the remote IKE peer, whereas the src field reveals the IP
address of a local interface. An active IKE SA is typically in the QM_IDLE state, as indicated by the state field.
The state field indicates the IKE negotiation state of an SA. An SA in the QM_IDLE state indicates that phase 1negotiations have completed and that the SA is ready for quick mode negotiation of an IPSec SA. Because
multiple SAs can exist between a particular source and destination, each SA is assigned a unique connection
ID, as shown in the connid field. You should issue the show crypto isakmp sa command without the active
keyword to display all current IKE SAs.
The show crypto ipsec securityassociation command displays the SA lifetime configured for an existing IPSec
SA. You can issue the crypto ipsec security association lifetime seconds seconds command from global
configuration mode to configure the SA lifetime. The command output below displays a default SA lifetime
configuration:
Security association lifetime: 4608000 kilobytes/3600 secondsCisco: Cisco IOS Security Command Reference: show crypto ipsec sa