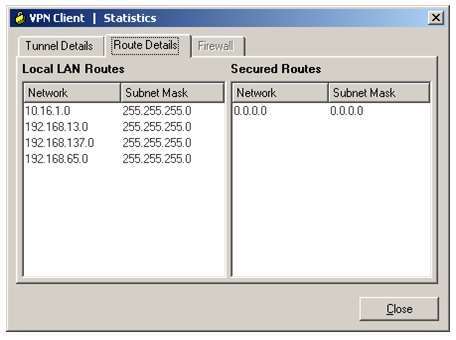
Which of the following can be determined from the Route Details tab of the VPN Client Statistics dialog box
shown above? (Select the best answer.)

A.
The VPN client cannot access devices on the local LAN.
B.
The VPN client is configured to use split tunneling.
C.
The VPN client is configured to use transparent tunneling.
D.
The VPN client cannot access devices on the 172.16.20.0/24 network.
Explanation:
The Route Details tab of the VPN Client Statistics dialog box displayed below indicates that the virtual private
network (VPN) client is configured to use split tunneling:By default, all traffic from a VPN client is passed through an encrypted tunnel to the VPN server. However, with
split tunneling, only traffic destined for a protected subnet is passed through the encrypted tunnel? all other
traffic is processed normally. You can define protected subnets on the VPN server by entering the network
address of each protected subnet on the Split Tunneling tab of the Group Policy window or by specifying an
access control list (ACL) that includes each protected subnet. When a client establishes a VPN session, the list
of protected subnets is passed from the VPN server to the VPN client as part of the session configuration
parameters.
Alternatively, the VPN client can be configured to pass all nonlocal traffic through an encrypted tunnel to the
VPN server. If the group policy on the VPN server permits local LAN access and the VPN client is configured to
allow local LAN access, all traffic that is not destined to the local LAN is sent through the encrypted tunnel. For
example, if the VPN client had a locally configured route to the 192.168.13.0/24 network, packets destined for
that network would be processed normally. However, any packets destined for a network not in the VPN client’s
routing table, such as the Internet, would pass through the encrypted tunnel to the VPN server. This
configuration is represented on the Route Details tab of the VPN Client Statistics dialog box shown below:The VPN Client Statistics dialog box does not indicate that the client cannot access devices on the
172.16.20.0/24 network. Because the 172.16.20.0/24 network is listed in the Secured Routes pane, traffic
destined for the 172.16.20.0/24 network will pass through the encrypted tunnel to the VPN server. However,
traffic destined for a network not in the Secured Routes pane, such as the Internet or the local LAN, will not
pass through the tunnel and will be processed normally.
Likewise, the VPN Client Statistics dialog box does not indicate that the client cannot access devices on the
local LAN. Because the router is configured for split tunneling, only traffic destined for a network in the Secured
Routes pane is passed through an encrypted tunnel to the VPN server. All other traffic, including local LAN
traffic, is processed normally.
You cannot determine from the Route Details tab of the VPN Client Statistics dialog box whether the client is
configured to use transparent tunneling. The Tunnel Details tab of the VPN Client Statistics dialog box indicates
whether the client is configured to use transparent tunneling. Transparent tunneling facilitates the creation of IP
Security (IPSec) tunnels through a firewall or Network Address Translation (NAT) device. When transparent
tunneling is enabled on the client, encrypted packets are encapsulated in Transmission Control Protocol (TCP)
or User Datagram Protocol (UDP) packets prior to transmission through the firewall or NAT device.Cisco: ASA/PIX: Allow Split Tunneling for VPN Clients on the ASA Configuration Example: Connect with the
VPN Client
CCNA Security 210260 Official Cert Guide, Chapter 8, Split Tunneling, pp. 227-228