HOTSPOT
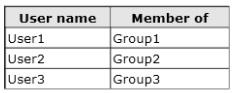
Your network contains an Active Directory domain named contoso.com. The domain contains the users shown
in the following table.
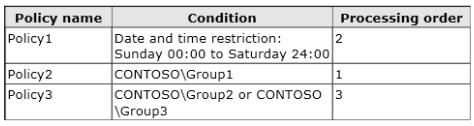
You have a Network Policy Server (NPS) server that has the network policies shown in the following table.
We also offer PRACTICE TEST SOFTWARE with Actual Exam Questions – Try free demo from our Website
User1, User2, and User3 plan to connect to the network by using a VPN. You need to identify which network
policy will apply to each user.
What should you identify?
To answer, select the appropriate policy for each user in the answer area.

Explanation:



User 1: Pol 2
User 2 and 3: Pol 1
0
0
how did you come up with user 2, and 3 in policy 1. im thinking policy 3 as users 2 and 3 are in groups 2 and 3
1
0
Alets’ answer is correct. The first condition that the user matches will be applied. The later conditions will be all ignored.
Below I post what I read in my reference ebook. It will help you understand how network policy works.
An NPS network policy evaluates remote connections based on the following three
components:
• Conditions
• Constraints
• Settings
If the conditions and constraints defi ned by the connection attempt match those confi gured in
the network policy, the remote access server will either allow or deny the connection and
confi gure additional settings, as defi ned by the policy. Every remote access policy has an Access
Permissions setting, which specifi es whether connections matching the policy should be
allowed or denied.
When a user attempts to connect to a remote access server, the following process takes place:
1. User attempts to initiate a remote access connection.
2. Remote Access server checks the conditions in the first configured NPS network policy.
3. If the conditions of this NPS network policy do not match, the Remote Access server
checks the next configured NPS network policies. It keeps checking each policy until it
finds a match or reaches the last policy.
4. Once the Remote Access Server finds an NPS network policy with conditions that match
the incoming connection attempt, the Remote Access server checks any constraints (such
as time of day or minimum encryption level) that have been configured for the policy.
5. If the connection attempt does not match any configured constraints, the Remote
Access Server denies the connection.
6. If the connection attempt matches both the conditions and the constraints of a particular
NPS network policy, the remote access server will allow or deny the connection,
based on the Access Permissions configured for that policy.
0
0
stupid question 🙂
0
0
the time restriction in policy 2 must mean that it blocks users access 24-7 ?
0
0
The policy 1 doesn’t say allow or denied. I hate to say ‘assume’ when it comes to these type of test, but can we assume that it means permitted 24-7?
0
0