Your network contains an Active Directory domain named contoso.com. The domain
contains a file server named Server1 that runs Windows Server 2012 R2.
You view the effective policy settings of Server1 as shown in the exhibit. (Click the Exhibit button.)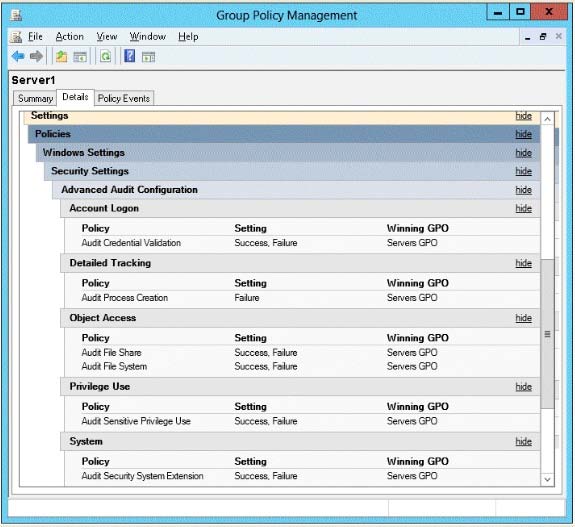
On Server1, you have a folder named C:\Share1 that is shared as Share1. Share1 contains
confidential data. A group named Group1 has full control of the content in Share1.
You need to ensure that an entry is added to the event log whenever a member of Group1
deletes a file in Share1.
What should you configure?

A.
the Audit File Share setting of Servers GPO
B.
the Sharing settings of C:\Share1
C.
the Audit File System setting of Servers GPO
D.
the Security settings of C:\Share1
Explanation:
You can use Computer Management to track all connections to shared resources on a
Windows Server 2008 R2 system.
Whenever a user or computer connects to a shared resource, Windows Server 2008 R2 lists
a connection in the Sessions node.File access, modification and deletion can only be tracked, if the object access auditing is
enabled you can see the entries in event log.
To view connections to shared resources, type net session at a command prompt or follow
these steps:
1. In Computer Management, connect to the computer on which you created the shared
resource.
2. In the console tree, expand System Tools, expand Shared Folders, and then select
Sessions. You can now view connections to shares for users and computers.
To enable folder permission auditing, you can follow the below steps:
1. Click start and run “secpol. msc” without quotes.
2. Open the Local Policies\Audit Policy
3. Enable the Audit object access for “Success” and “Failure”.
4. Go to target files and folders, right click the folder and select properties.
5. Go to Security Page and click Advanced.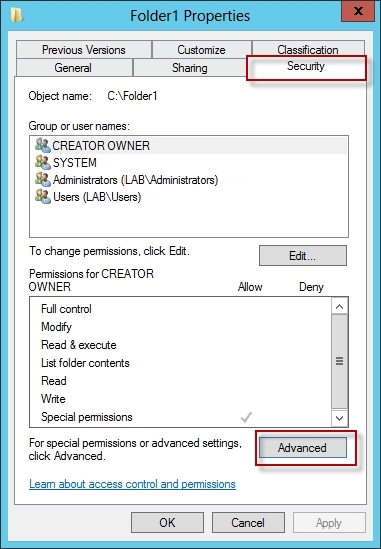
6. Click Auditing and Edit.
7. Click add, type everyone in the Select User, Computer, or Group.
8. Choose Apply onto: This folder, subfolders and files.
9. Tick on the box “Change permissions”
10. Click OK.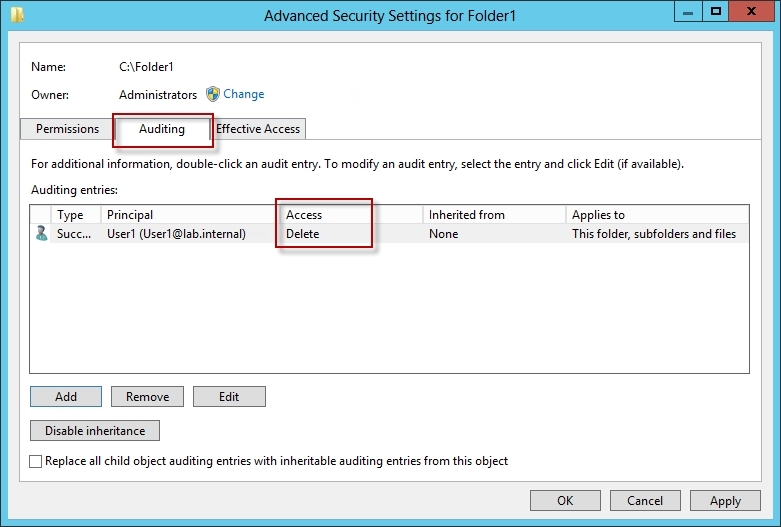
After you enable security auditing on the folders, you should be able to see the folder
permission changes in the server’s Security event log. Task Category is File System.
http: //social. technet. microsoft. com/Forums/en-US/winservergen/thread/13779c78-0c73-
4477-8014-f2eb10f3f10f/
http: //technet. microsoft. com/en-us/library/cc753927(v=ws. 10). aspx
http: //social. technet. microsoft. com/Forums/en-US/winservergen/thread/13779c78-0c73-
4477-8014-f2eb10f3f10f/
http: //support. microsoft. com/kb/300549
http: //www. windowsitpro. com/article/permissions/auditing-folder-permission-changes
http: //www. windowsitpro. com/article/permissions/auditing-permission-changes-on-a-folder




D from the advanced security setting auditing tab
0
0