HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain
contains 25 servers. All servers run Windows Server 2012 R2.
You need to create a Windows Firewall rule to prevent administrators from using Internet
Explorer to access the Internet while they are logged on interactively to the servers. The
solution must not prevent administrators from accessing websites on the internal network.
How should you configure the rule?
To answer, select the appropriate options in the answer area.
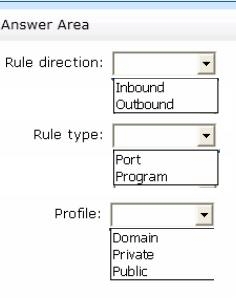




It seems during my testing that I cannot allow IE local access while blocking external access using any combination of these rules.
Outbound, program, domain results in everything being blocked (as all servers are on the domain).
Either Public or private have no effect, given the NIC is in the domain zone.
Port, without testing, can either stop 80 inbound resulting in the server failing to serve websites. Or can block ports above the reserved range resulting again in everything being blocked, not just internal and external sites but every single application that uses a randomly generated outbound port.
Forgive me, but I can’t see how any of these are correct without resulting in a blanket block for any IExplore.exe activity or no block whatsoever.
0
0
I suspect this is a trick-ish question. The question or answer area never defines if its a blocking rule.
If I assumed it was a blocking rule then I would not want to block outbound access on the domain profile. Leaving me to choose either the private or public profiles. In either case if I chose one over the other it would still allow access.
The logical conclusion I came to was that it was an allow rule. In that case the question parameters are met be the only obvious solution. Allow outbound access on the domain profile (internal network).
0
0
Tricky indeed.
I guess they use the “Allow Connection if it’s Secure” option to differentiate between external websites (no IPSec) and websites on the internal network (IPSec).
0
0
I agree with JonBan:
Create new outbound rule
Choose Program
Action: Allow the connection if it is secure–> This gives an extra menu option named Computers –>Choose Exceptions (skip this rule for connections to these computers
0
0
I have tested this in my lab, and in my opinion, the correct answer is: outbound – program – domain (same as the answer that was provided here).
I had 2 servers in my test environment, of which one was running the default IIS website (server A).
I then created a firewall rule on my second server (B) that blocks outbound connections for a program (location: %ProgramFiles% (x86)\Internet Explorer\iexplore.exe) when the computer is connected to the domain network.
This rule still allows me to connect to my IIS website on server A, but I can no longer connect to Google or any other website.
As usual with these questions, this one leaves some room for interpretation, and there are probably other solutions that might do the trick.
0
0
IT IS NOT A TRICKY QUESTION.
ANSWER:
BLOCK 🙂 OUTBOUND PROGRAM DOMAIN RULE
just create new one:
General tab – choose Block the connection radiobutton
Programs and services tab – This program: %ProgramFiles% (x86)\Internet Explorer\iexplore.exe OR %ProgramFiles%\Internet Explorer\iexplore.exe
SCOPE TAB (YES, MY DEAR FRIENDs) – Remote IP addresses section -> choose These IP addresses radiobutton -> then Add… button -> in a new window choose Predefined set of computers radiobutton and select Internet
DON’T TOUCH ANOTHER TABS (such as Remote computers tab 😉
IT WORKS AS EXPECTED !!!
0
0