A directory traversal (or path traversal) consists in exploiting insufficient security
validation/sanitization of user-supplied input file names, so that characters representing
“traverse to parent directory” are passed through to the file APIs. The goal of this attack is to
order an application to access a computer file that is not intended to be accessible. This
attack exploits a lack of security (the software is acting exactly as it is supposed to) as
opposed to exploiting a bug in the code.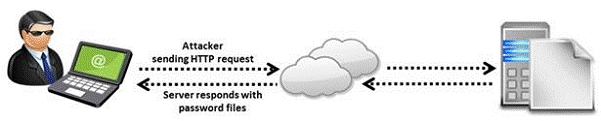
To perform a directory traversal attack, which sequence does a pen tester need to follow to
manipulate variables of reference files?

A.
dot-dot-slash (../) sequence
B.
Denial-of-Service sequence
C.
Brute force sequence
D.
SQL Injection sequence
Explanation:
Reference:
https://www.cs.ucsb.edu/~vigna/publications/2010_doupe_cova_vigna_dimva10.pdf(pae 7,
directory traversal)


A