Phishing is typically carried out by email spoofing or instant messaging and it often directs
users to enter details at a fake website whose look and feel are almost identical to the
legitimate one. Phishing is an example of social engineering techniques used to deceive
users, and exploits the poor usability of current web security technologies. Attempts to deal
with the growing number of reported phishing incidents include legislation, user training,
public awareness, and technical security measures.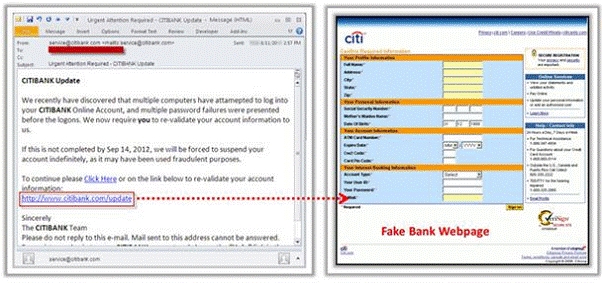
What characteristics do phishing messages often have that may make them identifiable?

A.
Invalid email signatures or contact information
B.
Suspiciously good grammar and capitalization
C.
They trigger warning pop-ups
D.
Suspicious attachments


C
Reference for this would be nice.
A, C and D can all be true, but none of them is guaranteed. The most identifiable characteristic is that the URL referenced does not link to the actual entity’s website. That answer is not available however.
The majority of phishing message do not contain attachments and may not trigger pop-ups.
https://www.owasp.org/index.php/Phishing#Do_not_use_pop-ups
Tricky one… I would go with A simply because an e-mail that pretends is from bank ‘x’ will most likely contain some contact information/e-mail signatures for bank ‘x’ that are false.
C and D are not very common.
A.
Invalid email signatures or contact information
=> A phishing email is usually sent using a “seems familiar” or “your acquaintance’s” email to lure you to click the link. For example, a real existent bank, for example Citi Bank, or Facebook, telling you that your account is suspended or something.
B.
Suspiciously good grammar and capitalization
=>not necessary.
C.
They trigger warning pop-ups
=>This is one of the characteristics of rogue advertisement or fake antivirus program you will see when browsing websites.
D.
Suspicious attachments
=>This is a better answer among the choices.
C? or D?
Module 15, Page 524
“Pop-ups trick users into clicking a hyperlink that redirects them to fake web pages asking for personal information.”
Therefore, according to ECSA courseware, C might be the right answer…
C is Correct ,It tricks User
Ref :ECSA V8 Module Social Engineering via Phishing Attachk