Which of the following password cracking techniques is used when the attacker has some information about the p
Which of the following password cracking techniques is used when the attacker has some
information about the password?
Which of the following is an application alert returned by a web application that helps an attacker guess a va
Which of the following is an application alert returned by a web application that helps an
attacker guess a valid username?
What is the table name?
A pen tester has extracted a database name by using a blind SQL injection. Now he begins
to test the table inside the database using the below query and finds the table:
http://juggyboy.com/page.aspx?id=1 ; IF (LEN(SELECT TOP 1 NAME from sysobjects
where xtype=’U’)=3) WAITFOR DELAY ’00:00:10′–
http://juggyboy.com/page.aspx?id=1 ; IF (ASCII(lower(substring((SELECT TOP 1 NAME
from sysobjects where xtype=char(85)),1,1)))=101) WAITFOR DELAY ’00:00:10′–
http://juggyboy.com/page.aspx?id=1 ; IF (ASCII(lower(substring((SELECT TOP 1 NAME
from sysobjects where xtype=char(85)),2,1)))=109) WAITFOR DELAY ’00:00:10′–
http://juggyboy.com/page.aspx?id=1 ; IF (ASCII(lower(substring((SELECT TOP 1 NAME
from sysobjects where xtype=char(85)),3,1)))=112) WAITFOR DELAY ’00:00:10’—
What is the table name?
what type of IDS is beingused?
When you are running a vulnerability scan on a network and the IDS cuts off your
connection, what type of IDS is beingused?
HTTP protocol specifies that arbitrary binary characters can be passed within the URL by using %xx notation, w
HTTP protocol specifies that arbitrary binary characters can be passed within the URL by
using %xx notation, where ‘xx’ is the
Which of the following appendices gives detailed lists of all the technical terms used in the report?
Which of the following appendices gives detailed lists of all the technical terms used in the report?
which of the following scanning techniques allow you to determine a port’s state without making a full conne
An external intrusion test and analysis identify security weaknesses and strengths of the
client’s systems and networks as they appear from outside the client’s security perimeter,
usually from the Internet. The goal of an external intrusion test and analysis is to
demonstrate the existence of known vulnerabilities that could be exploited by an external attacker.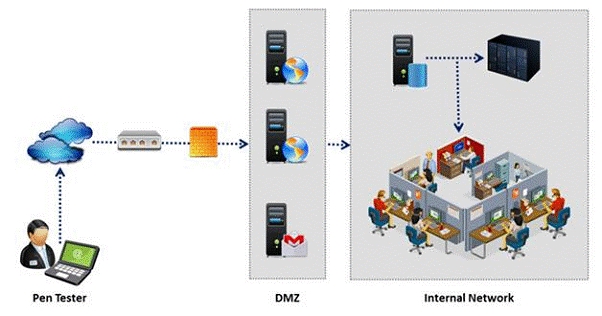
During external penetration testing, which of the following scanning techniques allow you to
determine a port’s state without making a full connection to the host?
Which of the following password cracking attacks tries every combination of characters until the password is b
Passwords protect computer resources and files from unauthorized access by malicious
users. Using passwords is the most capable and effective way to protect information and to
increase the security level of a company. Password cracking is the process of recovering
passwords from data that have been stored in or transmitted by a computer system to gain
unauthorized access to a system.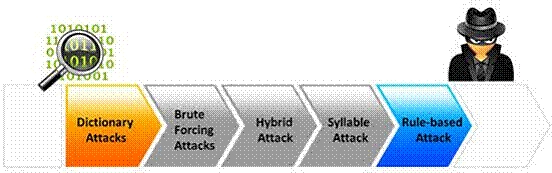
Which of the following password cracking attacks tries every combination of characters until
the password is broken?
What is the last step in preparing a Rules of Engagement (ROE) document?
Rules of Engagement (ROE) document provides certain rights and restriction to the test
team for performing the test and helps testers to overcome legal, federal, and policy-related
restrictions to use different penetration testing tools and techniques.
What is the last step in preparing a Rules of Engagement (ROE) document?
Which of the following is a framework of open standards developed by the Internet Engineering Task Force (IETF
Which of the following is a framework of open standards developed by the Internet
Engineering Task Force (IETF) that provides secure transmission of the sensitive data over
an unprotected medium, such as the Internet?

