Which of the following attacks can be detected with the help of wireless intrusion detection system (WIDS)?
A wireless intrusion detection system (WIDS) monitors the radio spectrum for the presence
of unauthorized, rogue access points and the use of wireless attack tools. The system
monitors the radio spectrum used by wireless LANs, and immediately alerts a systems
administrator whenever a rogue access point is detected. Conventionally it is achieved by
comparing the MAC address of the participating wireless devices. Which of the following
attacks can be detected with the help of wireless intrusion detection system (WIDS)?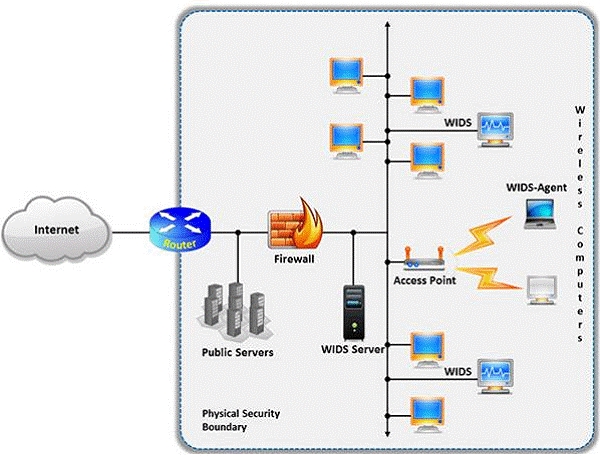
What are the two types of ‘white-box’ penetration testing?
Which of the following is not the SQL injection attack character?
Which of the following is not the SQL injection attack character?
Which of the following is the objective of Gramm-Leach-Bliley Act?
Which of the following is the objective of Gramm-Leach-Bliley Act?
Which of the following contents of a pen testing project plan addresses the strengths, weaknesses, opportuniti
Which of the following contents of a pen testing project plan addresses the strengths,
weaknesses, opportunities, and threats involved in the project?
Identify the level up to which the unknown traffic is allowed into the network stack
What characteristics do phishing messages often have that may make them identifiable?
Phishing is typically carried out by email spoofing or instant messaging and it often directs
users to enter details at a fake website whose look and feel are almost identical to the
legitimate one. Phishing is an example of social engineering techniques used to deceive
users, and exploits the poor usability of current web security technologies. Attempts to deal
with the growing number of reported phishing incidents include legislation, user training,
public awareness, and technical security measures.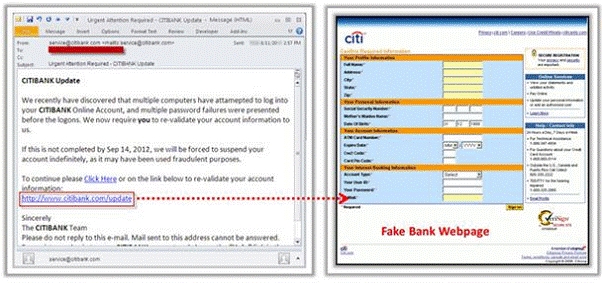
What characteristics do phishing messages often have that may make them identifiable?
Which of the following are the default ports used by NetBIOS service?
Which of the following are the default ports used by NetBIOS service?
What is the maximum value of a “tinyint” field in most database systems?
What is the maximum value of a “tinyint” field in most database systems?
What can a pen tester do to detect input sanitization issues?
Black-box testing is a method of software testing that examines the functionality of an
application (e.g. what the software does) without peering into its internal structures or
workings. Black-box testing is used to detect issues in SQL statements and to detect SQL
injection vulnerabilities.
Most commonly, SQL injection vulnerabilities are a result of coding vulnerabilities during the
Implementation/Development phase and will likely require code changes.
Pen testers need to perform this testing during the development phase to find and fix the
SQL injection vulnerability.
What can a pen tester do to detect input sanitization issues?