What is a goal of the penetration testing report?
Which of the following is the range for assigned ports managed by the Internet Assigned Numbers Authority (IAN
Which of the following is the range for assigned ports managed by the Internet Assigned
Numbers Authority (IANA)?
Identify the injection attack represented in the diagram below:
Which of the following approaches to vulnerability assessment relies on the administrator providing baseline o
What is the best way to protect web applications from parameter tampering attacks?
The Web parameter tampering attack is based on the manipulation of parameters
exchanged between client and server in order to modify application data, such as user
credentials and permissions, price and quantity of products, etc. Usually, this information is
stored in cookies, hidden form fields, or URL Query Strings, and is used to increase
application functionality and control. This attack takes advantage of the fact that many
programmers rely on hidden or fixed fields (such as a hidden tag in a form or a parameter in
a URL) as the only security measure for certain operations. Attackers can easily modify
these parameters to bypass the security mechanisms that rely on them.
What is the best way to protect web applications from parameter tampering attacks?
What does a vulnerability assessment identify?
What is this team called?
This is a group of people hired to give details of the vulnerabilities present in the system
found after a penetration test. They are elite and extremely competent penetration testers
and intrusion analysts. This team prepares a report on the vulnerabilities in the system,
attack methods, and how to defend against them.
What is this team called?
What type of attack would you launch after successfully deploying ARP spoofing?
ARP spoofing is a technique whereby an attacker sends fake (“spoofed”) Address
Resolution Protocol (ARP) messages onto a Local Area Network. Generally, the aim is to
associate the attacker’s MAC address with the IP address of another host (such as the
default gateway), causing any traffic meant for that IP address to be sent to the attacker
instead. ARP spoofing attack is used as an opening for other attacks.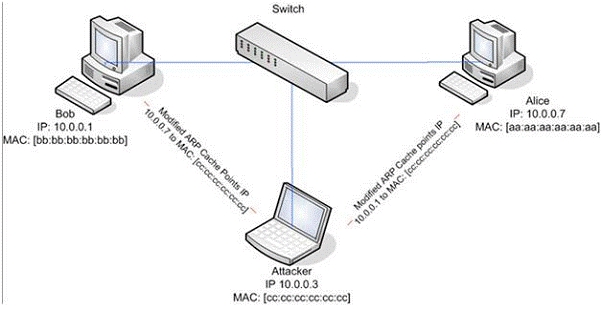
What type of attack would you launch after successfully deploying ARP spoofing?
Which agreement requires a signature from both the parties (the penetration tester and the company)?
Amazon Consulting Corporation provides penetration testing and managed security services
to companies. Legality and regulatory compliance is one of the important components in
conducting a successful security audit. Before starting a test, one of the agreements both the
parties need to sign relates to limitations, constraints, liabilities, code of conduct, and
indemnification considerations between the parties.
Which agreement requires a signature from both the parties (the penetration tester and the company)?






