Attackers create secret accounts and gain illegal access to resources using backdoor while
bypassing the authentication procedures. Creating a backdoor is a where an attacker
obtains remote access to a computer on a network.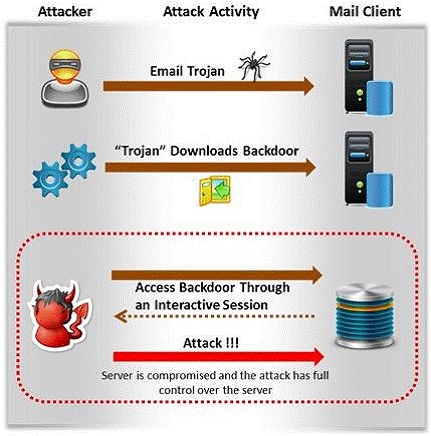
Which of the following techniques do attackers use to create backdoors to covertly gather
critical information about a target machine?

A.
Internal network mapping to map the internal network of the target machine
B.
Port scanning to determine what ports are open or in use on the target machine
C.
Sniffing to monitor all the incoming and outgoing network traffic
D.
Social engineering and spear phishing attacks to install malicious programs on the target
machine


D