Which of the following steps are required in an idle scan of a closed port?
Each correct answer represents a part of the solution. Choose all that apply.

A.
The attacker sends a SYN/ACK to the zombie.
B.
The zombie’s IP ID increases by only 1.
C.
In response to the SYN, the target sends a RST.
D.
The zombie ignores the unsolicited RST, and the IP ID remains unchanged.
E.
The zombie’s IP ID increases by 2.
Explanation:
Following are the steps required in an idle scan of a closed port:
1.Probe the zombie’s IP ID: The attacker sends a SYN/ACK to the zombie. The zombie, unaware
of the SYN/ACK, sends back a RST, thus disclosing its IP ID.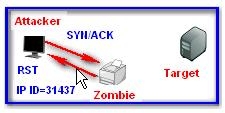
2.Forge a SYN packet from the zombie: In response to the SYN, the target sends a RST. The
zombie ignores the unsolicited RST, and the IP ID remains unchanged.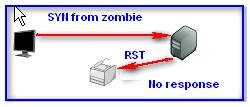
3.Probe the zombie’s IP ID again: The zombie’s IP ID has increased by only 1 since step 1. So the
port is closed.




