John visits an online shop that stores the IDs and prices of the items to buy in a cookie. After
selecting the items that he wants to buy, the attacker changes the price of the item to 1.
Original cookie values:
ItemID1=2
ItemPrice1=900
ItemID2=1
ItemPrice2=200
Modified cookie values:
ItemID1=2
ItemPrice1=1
ItemID2=1
ItemPrice2=1
Now, he clicks the Buy button, and the prices are sent to the server that calculates the total price.
Which of the following hacking techniques is John performing?

A.
Computer-based social engineering
B.
Man-in-the-middle attack
C.
Cookie poisoning
D.
Cross site scripting
Explanation:
John is performing cookie poisoning. In cookie poisoning, an attacker modifies the value of
cookies before sending them back to the server. On modifying the cookie values, an attacker can
log in to any other user account and can perform identity theft. The following figure explains how
cookie poisoning occurs: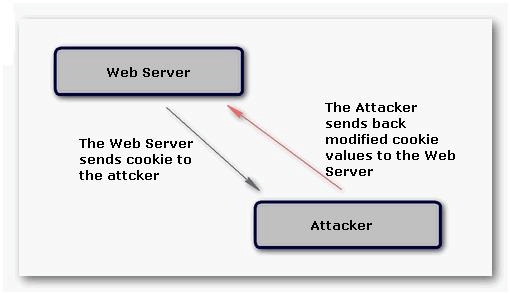
For example:
The attacker visits an online shop that stores the IDs and prices of the items to buy in a cookie.
After selecting the items that he wants to buy, the attacker changes the price of the item to 1.
Original cookie values:
ItemID1= 2
ItemPrice1=900
ItemID2=1
ItemPrice2=200
Modified cookie values:
ItemID1= 2
ItemPrice1=1
ItemID2=1
ItemPrice2=1
Now, the attacker clicks the Buy button and the prices are sent to the server that calculates the
total price.
Another use of a Cookie Poisoning attack is to pretend to be another user after changing the
username in the cookie values:
Original cookie values:
LoggedIn= True
Username = Mark
Modified cookie values:
LoggedIn= True
Username = Admin
Now, after modifying the cookie values, the attacker can do the admin login.
Answer option D is incorrect. A cross site scripting attack is one in which an attacker enters
malicious data into a Website. For example, the attacker posts a message that contains malicious
code to any newsgroup site. When another user views this message, the browser interprets this
code and executes it and, as a result, the attacker is able to take control of the user’s system.
Cross site scripting attacks require the execution of client-side languages such as JavaScript,
Java, VBScript, ActiveX, Flash, etc. within a user’s Web environment. With the help of a cross site
scripting attack, the attacker can perform cookie stealing, sessions hijacking, etc.


