Your network contains an Active Directory domain named contoso.com. All domain
controllers run Windows Server 2012 R2. The domain contains two domain controllers.
The domain controllers are configured as shown in the following table.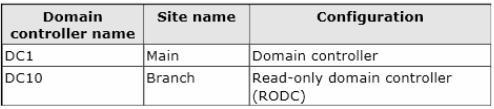
You configure a user named User1 as a delegated administrator of DC10.
You need to ensure that User1 can log on to DC10 if the network link between the Main site
and the Branch site fails.
What should you do?

A.
Add User1 to the Domain Admins group.
B.
On DC10, modify the User Rights Assignment in Local Policies.
C.
Run repadmin and specify the /prp parameter.
D.
On DC10, run ntdsutil and configure the settings in the Roles context.
Explanation:
repadmin /prp will allow the password caching of the local administrator to the RODC.


Be carefull this question is in different Versions in this test.
1
0
Hard One.
repadmin /prp add allow
Specifies the host name of the RODC. You can specify the single-label host name or the fully qualified domain name (FQDN). In addition, you can use an asterisk (*) as a wildcard character to specify multiple RODCs in one domain.
Specifies the name of the Security Principal that you want to Add to the Allowed List.
Adds the specified security principal to the msDS-RevealOnDemandGroup attribute that is associated with the RODC. (This attribute is also known as the Allowed List.)
0
0
Last Post didn’t come over correct. Missing the Parameters. This one makes more sense.
Repadmin /prp Add RODCName Allow PRINCIPALName
RODCName
Specifies the host name of the RODC. You can specify the single-label host name or the fully qualified domain name (FQDN). In addition, you can use an asterisk (*) as a wildcard character to specify multiple RODCs in one domain.
PRINCIPALName
Specifies the name of the security principal that you want to add to the Allowed List.
ADD
Adds the specified Security Principal to the msDS-RevealOnDemandGroup Attribute that is associated with the RODC. (This attribute is also known as the Allowed List.)
0
0
Repadmin /prp
Specifies the Password Replication Policy (PRP) for read-only domain controllers (RODCs).
2
0
https://technet.microsoft.com/en-us/library/cc770963.aspx
0
0
From my point this is a tricky question.
They are saying about : You configure a user named User1 as a delegated administrator of DC10.
So why do you think: repadmin /prp ?
Even MS said: You run the repadmin /prp command against a writable domain controller that runs Windows Server 2008 rather than an RODC.
https://technet.microsoft.com/en-us/library/cc835090.aspx
From windows 2008 we can delegate local administrator to RODC by:
ntdsutil and dsmgmt
So?
https://technet.microsoft.com/pl-pl/library/cc755310(v=ws.10).aspx
Using ntdsutil or dsmgmt to specify the delegated RODC administrator account is not recommended because the information is stored only locally on the RODC. Therefore, when you use ntdsutil local roles to delegate an administrator for the RODC […]
also here we have eplanation:
You can also configure role separation locally on the RODC after installation by using the Ntdsutil or Dsmgmt command line tools’ local roles option.
http://windowsitpro.com/security/q-how-can-i-delegate-administrator-role-given-rodc-single-administrator-account
For me this a MS trick to lead us to bad track.
My answer:
D.
On DC10, run ntdsutil and configure the settings in the Roles context.
Roles context = local roles option.
What do you think ?
0
0
answer is C. reason being is that you have just configured the user so AD has not had a chance to replicate those changes so c is right
0
0
should have added you delegate user 1 on a writeable dc
0
0
Answer is B.
You give a user account the “log on locally” rights.
This allows someone to log on to the sever to help with troubleshooting. Doesn’t need to be a domain account.
0
0
After further thought, this is my opinion…
it can’t be B because although you can give them logon locally rights, if the RODC cannot communicate with a writeable DC then the account cannot be authenticated without the password being cached.
But then again, does the user being a designated administrator give them the logon locally permissions or will we also need to do that? If so it would be both B and C
0
0
I am going with C
0
0
I meant give a “local user” log on local rights not a domain account. I got this from CBT Nuggets Video. That way if it is cut off from the network you still have a local account that can log on to the server to sort. Install new network card drivers etc.
Because the account is a local one, if the RODC was stolen it would not contain any domain passwords, so this method is the most secure.
0
0
There is same question, but with diffirent answers:
A. Add User1 to the Domain Admins group.
B. On DC10, run ntdsutil and configure the settings in the Roles context.
C. Run repadmin and specify the /prp parameter.
D. On DC1, modify the User Rights Assignment in Default Domain Controllers Group Policy object (GPO).
Answer: D
Explanation:
Modify the following policy: Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Allow log on locally
Note:
* User Rights Assignment policies determines which users or groups have logon rights or
privileges on the computer.
* Delegated administrator accounts gain local administrative permissions to the RODC. These users can operate with privileges equivalent to the local computer’s Administrators group. They are not members of the Domain Admins or the domain built-in Administrators groups. This option is useful for delegating branch office administration without giving out domain administrative permissions. Configuring delegation of administration is not required.
So It could be answere B to this question.
0
0
http://www.gatepoint.ch/cmdreferenz/html/cb82e949-9039-4763-9d29-fdc6ce42770a.htm
The following command caches the password for the user account named MikeDan on the domain controller named br1-rodc1:
repadmin /prp add br1-rodc1 allow cn=MikeDan,ou=user-groups,dc=contoso,dc=com
That’s what we’re looking for here right?
0
0
The answer is C because if you take the time to read this article, Microsoft tells you to NOT STORE the password locally on the machine. It actually tells you to create a security group and then assign the user(s) to that group.
https://technet.microsoft.com/en-us/library/cc755310%28v=ws.10%29.aspx
“So that the delegated RODC administrator can log on to the RODC when the wide area network (WAN) link to the hub site domain controller is not available, the delegated RODC administrator account password must be cached on the RODC. Note that the delegated RODC administrator account is not allowed to be cached on an RODC by default. Therefore, you have to modify the default PRP to allow the password to be cached, cache the password, and the recache it after every password change for successful logon to the RODC when the WAN is not available or a writable domain controller cannot be contacted. You must do this for every member of the security group that you specify as an administrator of the RODC.”
And yes you’re welcome Hassan 🙂
1
0
Thanks, after reading that and some other things in that link, it s clear that answer has to be C.
0
0