You need to recommend a solution so that marketing users print documents to Printer1 by default
###BeginCaseStudy###
Case Study: 1
Consolidated Messenger
Scenario:
You are an enterprise desktop support technician for Consolidated Messenger.
Network Configuration
The company has three offices named Office1, Office2, and Office3. The offices connect to
each other over the Internet by using VPN connections. Each office has an 802.11g wireless
access point. All wireless access points are configured to use Radius01 for authentication.
Active Directory Configuration
The network contains one Active Directory domain named consolidatedmessenger.com. The
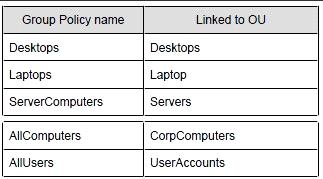
relevant organizational unit structure is shown in the following diagram.
The relevant Group Policy objects (GPOs) in the domain are configured as shown in the
following table.
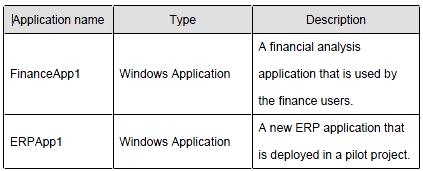
Applications
The relevant applications on the network are shown in the following table.
Server Configuration
The relevant servers are configured as shown in the following table.
Client Configuration
Each office has 500 desktop computers that run Windows 7 Enterprise. There are 250 mobile
users that travel regularly between all three offices. The mobile users have laptop computers
that run Windows 7 Enterprise. To prevent the spread of malware, the company restricts the
use of USB devices and only allows the use of approved USB storage devices.
Printers
The marketing group has several printers that are shared on File01. A shared printer name
Printer1 is a high-performance, black-and-white printer. A shared printer named Printer2 is a
high-definition, photo-quality, color printer. Printer2 should only be used to print marketing
brochures.
###EndCaseStudy###
The help desk reports that users in the Marketing OU print draft documents, e-mails, and other
miscellaneous documents on Printer2. You need to recommend a solution so that marketing users
print documents to Printer1 by default. What should you do?
What should you recommend?
###BeginCaseStudy###
Case Study: 1
Consolidated Messenger
Scenario:
You are an enterprise desktop support technician for Consolidated Messenger.
Network Configuration
The company has three offices named Office1, Office2, and Office3. The offices connect to
each other over the Internet by using VPN connections. Each office has an 802.11g wireless
access point. All wireless access points are configured to use Radius01 for authentication.
Active Directory Configuration
The network contains one Active Directory domain named consolidatedmessenger.com. The
relevant organizational unit structure is shown in the following diagram.
The relevant Group Policy objects (GPOs) in the domain are configured as shown in the
following table.
Applications
The relevant applications on the network are shown in the following table.
Server Configuration
The relevant servers are configured as shown in the following table.
Client Configuration
Each office has 500 desktop computers that run Windows 7 Enterprise. There are 250 mobile
users that travel regularly between all three offices. The mobile users have laptop computers
that run Windows 7 Enterprise. To prevent the spread of malware, the company restricts the
use of USB devices and only allows the use of approved USB storage devices.
Printers
The marketing group has several printers that are shared on File01. A shared printer name
Printer1 is a high-performance, black-and-white printer. A shared printer named Printer2 is a
high-definition, photo-quality, color printer. Printer2 should only be used to print marketing
brochures.
###EndCaseStudy###
The Office1 network link is brought offline for emergency maintenance. Users in Office2 and Office3
report that they cannot connect to the wireless network. You need to recommend changes to
ensure that users in all offices can connect to the wireless network if a WAN link fails. What should
you recommend?
You need to ensure that users can save data on the USB flash drives
###BeginCaseStudy###
Case Study: 1
Consolidated Messenger
Scenario:
You are an enterprise desktop support technician for Consolidated Messenger.
Network Configuration
The company has three offices named Office1, Office2, and Office3. The offices connect to
each other over the Internet by using VPN connections. Each office has an 802.11g wireless
access point. All wireless access points are configured to use Radius01 for authentication.
Active Directory Configuration
The network contains one Active Directory domain named consolidatedmessenger.com. The
relevant organizational unit structure is shown in the following diagram.
The relevant Group Policy objects (GPOs) in the domain are configured as shown in the
following table.
Applications
The relevant applications on the network are shown in the following table.
Server Configuration
The relevant servers are configured as shown in the following table.
Client Configuration
Each office has 500 desktop computers that run Windows 7 Enterprise. There are 250 mobile
users that travel regularly between all three offices. The mobile users have laptop computers
that run Windows 7 Enterprise. To prevent the spread of malware, the company restricts the
use of USB devices and only allows the use of approved USB storage devices.
Printers
The marketing group has several printers that are shared on File01. A shared printer name
Printer1 is a high-performance, black-and-white printer. A shared printer named Printer2 is a
high-definition, photo-quality, color printer. Printer2 should only be used to print marketing
brochures.
###EndCaseStudy###
The company purchases 500 USB flash drives from a new hardware vendor and distributes them to
the users. The help desk reports that the users are unable to access the new USB flash drives. You
need to ensure that users can save data on the USB flash drives. What should you do?
What should you recommend?
###BeginCaseStudy###
Case Study: 2
City Power & Light
Scenario:
You are an enterprise desktop support technician for City Power & Light. City Power &
Light is a utility company. The company has a main office and a branch office. The main
office is located in Toronto. The branch office is located in Boston. The main office has
1,000 employees. The branch office has 10 employees.
Active Directory Configuration
The network contains a single Active Directory domain named cpandl.com. The functional
level of the forest is Windows Server 2008 R2.
Server Configuration
All servers run Windows Server 2008 R2. The relevant servers in the main office are
configured as shown in the following table.
All computers in the main office are configured to use DHCP. All computers in the branch
office are configured to use static IP addresses.
User Information
• All user accounts are standard user accounts.
• All client computers run Windows 7 Enterprise.
• Each portable computer has a PPT P-based VPN connection to the internal network.
Corporate Security Guidelines
• All users must be granted the least privileges possible.
• All locally stored documents must be encrypted by using Encrypting File System
(EFS).
• The hard disk drives on all port able computers must be encrypted by using Windows
BitLocker Drive Encryption (BitLocker).
• All encryption certificates must be stored on smart cards.
###EndCaseStudy###
The company is deploying a new application. When users attempt to install the application, they
receive an error message indicating that they need administrative privileges to install it. You need to
recommend a solution to ensure that users can install the application. The solution must adhere to
the corporate security guidelines. What should you recommend?
What should you recommend?
###BeginCaseStudy###
Case Study: 2
City Power & Light
Scenario:
You are an enterprise desktop support technician for City Power & Light. City Power &
Light is a utility company. The company has a main office and a branch office. The main
office is located in Toronto. The branch office is located in Boston. The main office has
1,000 employees. The branch office has 10 employees.
Active Directory Configuration
The network contains a single Active Directory domain named cpandl.com. The functional
level of the forest is Windows Server 2008 R2.
Server Configuration
All servers run Windows Server 2008 R2. The relevant servers in the main office are
configured as shown in the following table.
All computers in the main office are configured to use DHCP. All computers in the branch
office are configured to use static IP addresses.
User Information
• All user accounts are standard user accounts.
• All client computers run Windows 7 Enterprise.
• Each portable computer has a PPT P-based VPN connection to the internal network.
Corporate Security Guidelines
• All users must be granted the least privileges possible.
• All locally stored documents must be encrypted by using Encrypting File System
(EFS).
• The hard disk drives on all port able computers must be encrypted by using Windows
BitLocker Drive Encryption (BitLocker).
• All encryption certificates must be stored on smart cards.
###EndCaseStudy###
Several mobile users access the Internet by using cellular connections. The help desk reports a high
volume of calls from mobile users who report the following connection problems:
• When their cellular connections fail, their VPN connections also fail.
• When their cellular connections are reestablished, they must manually connect to the VPN
server.
You need to recommend a solution to ensure that the VPN connections are automatically
reestablished. What should you recommend?
What should you instruct the help desk to do on the portable computers?
###BeginCaseStudy###
Case Study: 2
City Power & Light
Scenario:
You are an enterprise desktop support technician for City Power & Light. City Power &
Light is a utility company. The company has a main office and a branch office. The main
office is located in Toronto. The branch office is located in Boston. The main office has
1,000 employees. The branch office has 10 employees.
Active Directory Configuration
The network contains a single Active Directory domain named cpandl.com. The functional
level of the forest is Windows Server 2008 R2.
Server Configuration
All servers run Windows Server 2008 R2. The relevant servers in the main office are
configured as shown in the following table.
All computers in the main office are configured to use DHCP. All computers in the branch
office are configured to use static IP addresses.
User Information
• All user accounts are standard user accounts.
• All client computers run Windows 7 Enterprise.
• Each portable computer has a PPT P-based VPN connection to the internal network.
Corporate Security Guidelines
• All users must be granted the least privileges possible.
• All locally stored documents must be encrypted by using Encrypting File System
(EFS).
• The hard disk drives on all port able computers must be encrypted by using Windows
BitLocker Drive Encryption (BitLocker).
• All encryption certificates must be stored on smart cards.
###EndCaseStudy###
Five users from the main office travel to the branch office. The users bring their portable computers.
The help desk reports that the users are unable to access any network resources from the branch
office. Branch office users can access the network resources. You need to ensure that the main office
users can access all network resources by using their portable computers in the branch office. The
solution must adhere to the corporate security guidelines. What should you instruct the help desk to
do on the portable computers?
You need to ensure that the Connection to a Workplace Using DirectAccess troubleshooter functions properly
###BeginCaseStudy###
Case Study: 2
City Power & Light
Scenario:
You are an enterprise desktop support technician for City Power & Light. City Power &
Light is a utility company. The company has a main office and a branch office. The main
office is located in Toronto. The branch office is located in Boston. The main office has
1,000 employees. The branch office has 10 employees.
Active Directory Configuration
The network contains a single Active Directory domain named cpandl.com. The functional
level of the forest is Windows Server 2008 R2.
Server Configuration
All servers run Windows Server 2008 R2. The relevant servers in the main office are
configured as shown in the following table.
All computers in the main office are configured to use DHCP. All computers in the branch
office are configured to use static IP addresses.
User Information
• All user accounts are standard user accounts.
• All client computers run Windows 7 Enterprise.
• Each portable computer has a PPT P-based VPN connection to the internal network.
Corporate Security Guidelines
• All users must be granted the least privileges possible.
• All locally stored documents must be encrypted by using Encrypting File System
(EFS).
• The hard disk drives on all port able computers must be encrypted by using Windows
BitLocker Drive Encryption (BitLocker).
• All encryption certificates must be stored on smart cards.
###EndCaseStudy###
Users report that their DirectAccess connections fail. You instruct the help desk to tell the users to
run the Connection to a Workplace Using DirectAccess troubleshooter. The help desk reports that
the Connection to a Workplace Using DirectAccess troubleshooter fails to function. You need to
ensure that the Connection to a Workplace Using DirectAccess troubleshooter functions properly.
What should you do?
Which tool should you use?
###BeginCaseStudy###
Case Study: 2
City Power & Light
Scenario:
You are an enterprise desktop support technician for City Power & Light. City Power &
Light is a utility company. The company has a main office and a branch office. The main
office is located in Toronto. The branch office is located in Boston. The main office has
1,000 employees. The branch office has 10 employees.
Active Directory Configuration
The network contains a single Active Directory domain named cpandl.com. The functional
level of the forest is Windows Server 2008 R2.
Server Configuration
All servers run Windows Server 2008 R2. The relevant servers in the main office are
configured as shown in the following table.
All computers in the main office are configured to use DHCP. All computers in the branch
office are configured to use static IP addresses.
User Information
• All user accounts are standard user accounts.
• All client computers run Windows 7 Enterprise.
• Each portable computer has a PPT P-based VPN connection to the internal network.
Corporate Security Guidelines
• All users must be granted the least privileges possible.
• All locally stored documents must be encrypted by using Encrypting File System
(EFS).
• The hard disk drives on all port able computers must be encrypted by using Windows
BitLocker Drive Encryption (BitLocker).
• All encryption certificates must be stored on smart cards.
###EndCaseStudy###
The company implements a data recovery agent (DRA) for Bitlocker. A portable computer fails. The
help desk reports that it is unable to use the DRA to recover the data from the computer’s hard disk
drive. You need to ensure that the DRA can be used to recover data from the hard disk drives of all
portable computers. Which tool should you use?
You need to achieve this goal by using the minimum amount of administrative effort
###BeginCaseStudy###
Case Study: 3
A)
Datum Corporation
Scenario:
You are an enterprise desktop support technician for A. Datum Corporation.
Active Directory Configuration
The company has three offices. The offices are configured as shown in the following table.
The network contains a single Active Directory domain named adatum.com. Two Group
Policy objects (GPOs) are configured as shown in the following table.
The relevant servers in the main office are configured as shown in the following table.
Wireless Network
A wireless network is implemented in the main office. The wireless network is configured to
use WPA2-Enterprise security.
Client Configuration
All client computers run Windows 7 Enterprise and are configured to use DHCP. Windows
Firewall is disabled on all client computers. All computers in the research department have
Windows XP Mode and Windows Virtual PC installed. You deploy a custom Windows XP
Mode image to the research department computers. An application named App1 is installed
in the image.
Each research department computer has the following hardware:
• 4 GB of RAM
• Intel Core i7 processor
• 500 -GB hard disk drive
Corporate Security Policy
The corporate security policy includes the following requirements:
• Users without domain accounts must be denied access to internal servers.
• All connections to the company’s wireless access points must be encrypted.
• Only employees can be configured to have user accounts in the Active Directory
domain.
• The hard disk drives on all portable computers must be encrypted by using Windows
BitLocker Drive Encryption (BitLocker).
###EndCaseStudy###
Users in the research department report that they cannot run App1 or Windows XP Mode. You need
to ensure that all research department users can run App1. You need to achieve this goal by using
the minimum amount of administrative effort. What should you do?
What are two possible ways to achieve this goal?
###BeginCaseStudy###
Case Study: 3
A)
Datum Corporation
Scenario:
You are an enterprise desktop support technician for A. Datum Corporation.
Active Directory Configuration
The company has three offices. The offices are configured as shown in the following table.
The network contains a single Active Directory domain named adatum.com. Two Group
Policy objects (GPOs) are configured as shown in the following table.
The relevant servers in the main office are configured as shown in the following table.
Wireless Network
A wireless network is implemented in the main office. The wireless network is configured to
use WPA2-Enterprise security.
Client Configuration
All client computers run Windows 7 Enterprise and are configured to use DHCP. Windows
Firewall is disabled on all client computers. All computers in the research department have
Windows XP Mode and Windows Virtual PC installed. You deploy a custom Windows XP
Mode image to the research department computers. An application named App1 is installed
in the image.
Each research department computer has the following hardware:
• 4 GB of RAM
• Intel Core i7 processor
• 500 -GB hard disk drive
Corporate Security Policy
The corporate security policy includes the following requirements:
• Users without domain accounts must be denied access to internal servers.
• All connections to the company’s wireless access points must be encrypted.
• Only employees can be configured to have user accounts in the Active Directory
domain.
• The hard disk drives on all portable computers must be encrypted by using Windows
BitLocker Drive Encryption (BitLocker).
###EndCaseStudy###
Users in branch office 1 report that they fail to access the company’s intranet Web site located on
Web1. They also fail to access Web sites on the Internet. A desktop support technician restarts a
desktop computer in branch office 1 and discovers the IP configuration shown in the following
screenshot.
You need to resolve the network connectivity issue. What are two possible ways to achieve this
goal? (Each correct answer presents a complete solution. Choose two.)