What procedures should take place to restore a system and its data files after a system failure?
What procedures should take place to restore a system and its data files after a system failure?
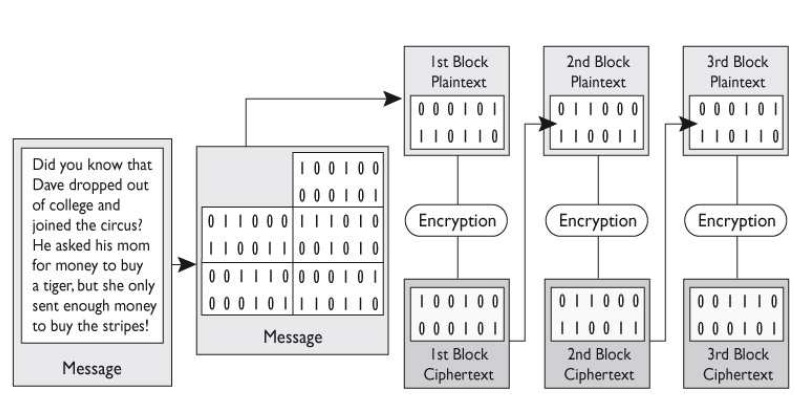
Which mode does the graphic that follows portray?
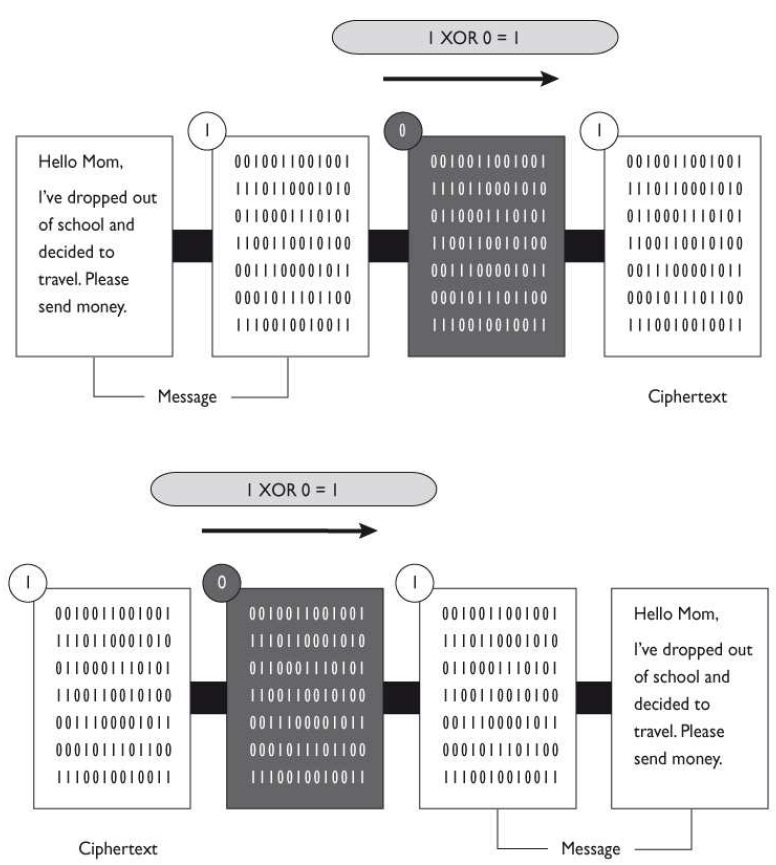
What type of technology is shown in the graphic that follows?
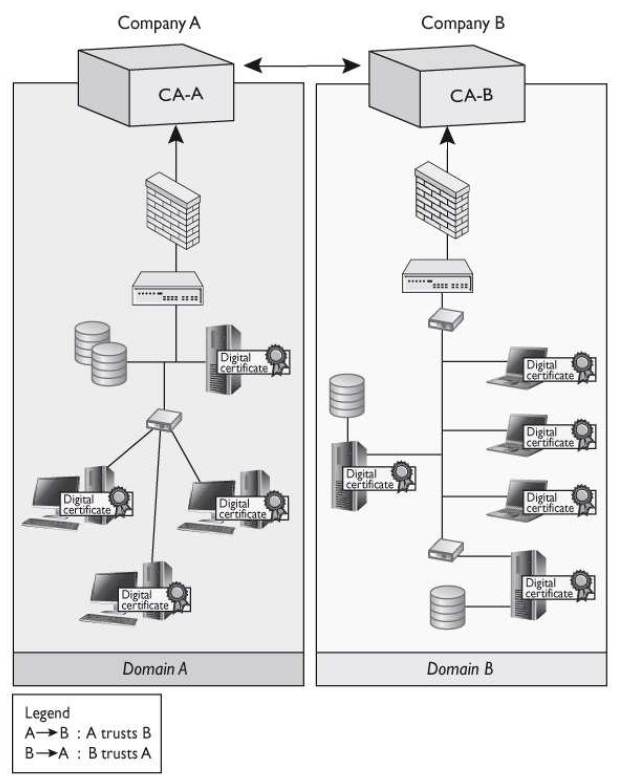
Which architecture does the graphic that follows represent?
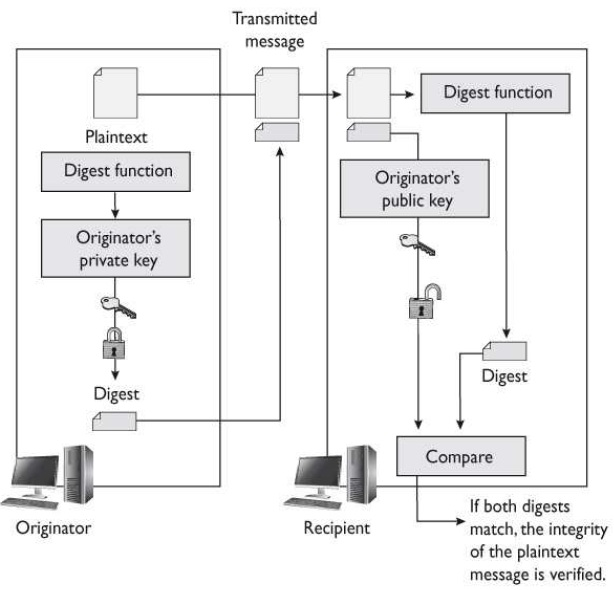
What is represented in the graphic that follows?
What do the SA values in the graphic of IPSec that follows represent?
Which of the following correctly describes these technologies?
End-to-end encryption is used by users, and link encryption is used by service providers. Which of the following correctly describes these technologies?
Which of the following correctly describes a CRL and OSCP?
The CA is responsible for revoking certificates when necessary. Which of the following correctly describes a CRL and OSCP?
Which of the following best describes what takes place during an SSL connection setup process?
SSL is a de facto protocol used for securing transactions that occur over untrusted networks. Which of the following best describes what takes place during an SSL connection setup process?
Advanced Encryption Standard is an algorithm used for which of the following?
Advanced Encryption Standard is an algorithm used for which of the following?