You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest domain-based network. The company has recently provided fifty laptops to its sales team members. You are required to configure an 802.11 wireless network for the laptops. The sales team members must be able to use their data placed at a server in a cabled network. The planned network should be able to handle the threat of unauthorized access and data interception by an unauthorized user. You are also required to prevent the sales team members from communicating directly to one another. Which of the following actions will you perform to accomplish the task? Each correct answer represents a complete solution. Choose all that apply.

A.
Configure the wireless network to use WEP encryption for the data transmitted over a wireless network.
B.
Implement the IEEE 802.1X authentication for the wireless network.
C.
Implement the open system authentication for the wireless network.
D.
Using group policies, configure the network to allow the wireless computers to connect to the ad hoc networks only.
E.
Using group policies, configure the network to allow the wireless computers to connect to the infrastructure networks only.
Explanation:
In order to enable wireless networking, you have to install access points in various areas of your office building. These access points generate omni directional signals to broadcast network traffic. nauthorized users can intercept these packets. Hence, security is the major concern for a wireless network. The two primary threats are unauthorized access and data interception. In order to accomplish the task, you will have to take the following steps:
Using group policies, configure the network to allow the wireless computers to connect to the infrastructure networks only. This will prevent the sales team members from communicating directly to one another.Implement the IEEE 802.1X authentication for the wireless network. This will allow only authenticated users to access the network data and resources.Configure the wireless network to use WEP encryption for data transmitted over a wireless network. This will encrypt the network data packets transmitted over wireless connections. Although WEP encryption does not prevent intruders from capturing the packets, it prevents them from reading the data inside.
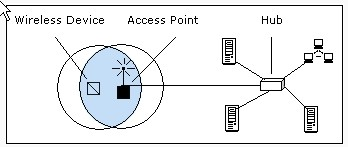
What is infrastructure network?
Infrastructure is a basic topology of a wireless network. An infrastructure network consists of an access point that connects wireless devices to the standard cable network. An access point is connected to the cabled network through a cable and it generates omni directional signals. When wireless devices come within the range of the access point, they are able to communicate with the cabled local area network.The access point works as a central bridge device to include wireless devices in the cabled LAN.
What is IEEE 802.1X authentication?
The IEEE 802.1X standard defines a method of authenticating and authorizing users to connect to an IEEE 802 LAN. It blocks users from accessing the network on the failure of authentication. IEEE 802.1X supports the Extensible Authentication Protocol-Transport Level Security (EAP-TLS) and Protected EAP-Microsoft Challenge Handshake Authentication Protocol version 2 (PEAP-MS-CHAP v2) protocols. In the IEEE802.1X authentication system, an access point receives a connection request from a wireless client and forwards the request to the RADIUS server. The RADIUS server then uses the Active Directory database to determine whether the client should be granted access to the network.
What is WEP?
Wired Equivalent Privacy (WEP) is a security protocol for wireless local area networks (WLANs). It has two components, authentication and encryption. It provides security, which is equivalent to wired networks, for wireless networks. WEP encrypts data on a wireless network by using a fixed secret key. WEP incorporates a checksum in each frame to provide protection against the attacks that attempt to reveal the key stream. Answer option C is incorrect. Open System authentication is the default authentication method used by 802.11 devices. But, in fact, it provides no authentication at all. It exchanges messages between the two wireless devices without using any password or keys. A device configured to use the Open System authentication cannot refuse to authenticate another device. Answer option D is incorrect. The ad hoc networks enable users to communicate directly to one another, whereas the question clearly states that you should prevent the sales team members from communicating directly to one another.
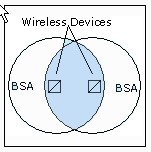
What is ad hoc network?
Ad hoc is a basic topology of a wireless network. An ad hoc network consists of two or more wireless devices that communicate directly with each other. The wireless local area network (WLAN) network interface adapters in the wireless devices generate omni directional signals within a limited range called basic service area (BSA). When two wireless devices come within the range of each other, they immediately form a two-node network and are able to communicate with each other.An ad hoc network is non-transitive.


ABD
0
0