what purpose?
In Cisco IDM, the Configuration > Sensor Setup > SSH > Known Host Keys screen is used for
what purpose?
Complete the following tasks:
What is not the advantage of Cisco Security MARS?
The Cisco Security Monitoring, Analysis and Response System (Cisco Security MARS) is an
appliance-based, all-inclusive solution that provides unmatched insight and control of your existing
security deployment. What is not the advantage of Cisco Security MARS?
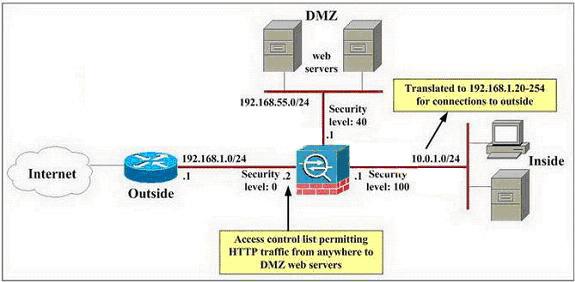
What is the reason that the contractors are able to surf the Internet from the DMZ servers?
John works as a network administrator .
According to the exhibit, the only traffic that John would like to allow through the corporate Cisco
ASA adaptive security appliance is inbound HTTP to the DMZ network and all traffic from the
inside network to the outside network. John also has configured the Cisco ASA adaptive security
appliance, and access through it is now working as expected with one exception: contractors
working on the DMZ servers have been surfing the Internet from the DMZ servers, which (unlike
other Company XYZ hosts) are using public, routable IP addresses. Neither NAT statements nor
access lists have been configured for the DMZ interface.
What is the reason that the contractors are able to surf the Internet from the DMZ servers?
(Note: The 192.168.X.XIP addresses are used to represent routable public IP addresses even
though the 192.168.1.0 network is not actually a public routable network.)
Which command will redirect HTTP traffic bound for the DMZ web server to its real IP address of 10.10.11.4?
An internet user is sending HTTP traffic to a DMZ server with the external address of 192.168.1.4.
Which command will redirect HTTP traffic bound for the DMZ web server to its real IP address of
10.10.11.4?
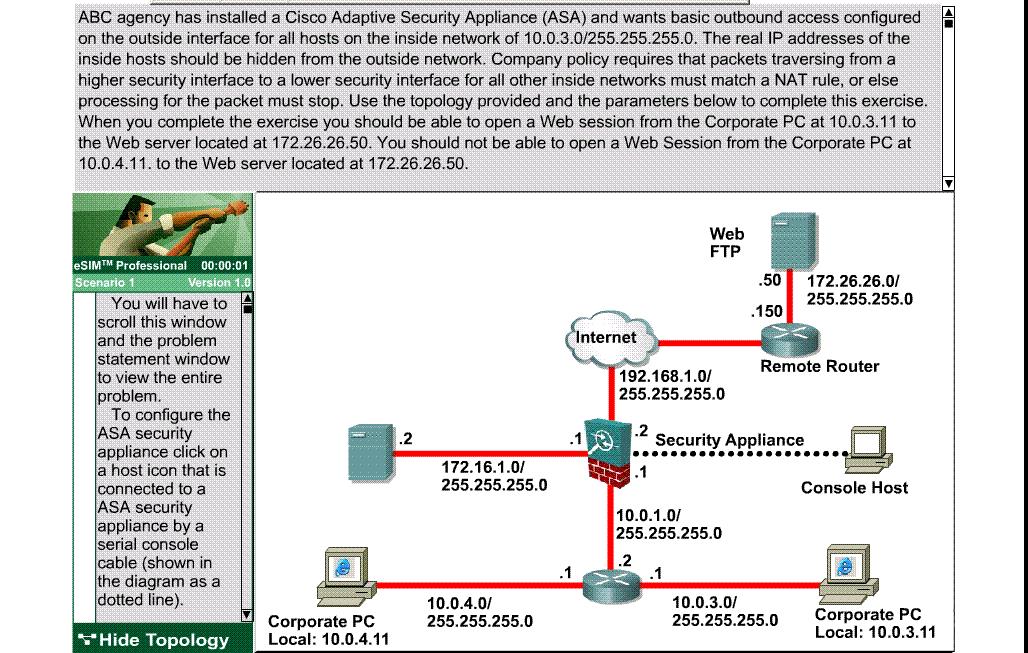
Company policy requires that packets traversing from a higher security interface to a lower security interface
What two steps must you perform to initialize a Cisco IPS Sensor appliance?
What two steps must you perform to initialize a Cisco IPS Sensor appliance? (Choose two.)
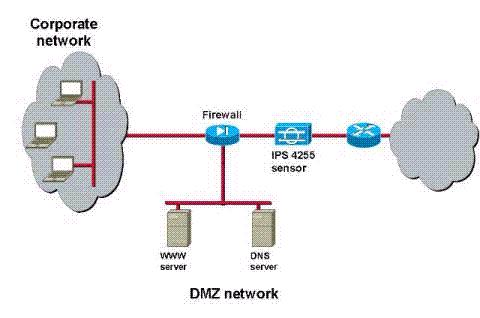
Which two should you use to accomplish your goal in the most time-efficient manner?
Refer to the exhibit. You are the security administrator for the network in the exhibit. You want
your inline Cisco IPS 4255 sensor to drop packets that pose the most severe risk to your network,
especially to the servers on your DMZ.
Which two should you use to accomplish your goal in the most time-efficient manner? (Choose
two.)
Identify three components of the anit-X defense pillar.
Adaptive Threat Defense or ATD encompasses three areas: Anti-X defense, application security
and network control and containment. Identify three components of the anit-X defense pillar.
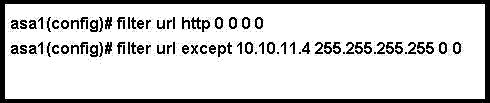
Which two tasks do these commands accomplish?
Refer to the exhibit. The adaptive security appliance administrator needs to filter a single website
on a host with the IP address 10.10.11.4, but allow access to all other websites. The administrator
enters the commands shown and then executes them.
Which two tasks do these commands accomplish? (Choose two.)