What is an appropriate action to take?
Which description is true about the hybrid user authentication model for remote-access IPSec VPNs?
Which description is true about the hybrid user authentication model for remote-access IPSec
VPNs?
What is used to perform password recovery for the "cisco" admin account on a Cisco IPS 4200 Series S
What is used to perform password recovery for the “cisco” admin account on a Cisco IPS 4200
Series Sensor?
Match each evasive technique on the left to the proper description on the right.
Which two of the following settings can be monitored by the Cisco Security Agent (release 5.2 and later) to co
Which two of the following settings can be monitored by the Cisco Security Agent (release 5.2 and
later) to control user’s wireless access? (Choose two.)
Which one of the following commands can reactivate the primary adaptive security appliance and restore it to a
Tom works as a network administrator. The primary adaptive security appliance in an
active/standby failover configuration failed, so the secondary adaptive security appliance was
automatically activated. Tom then fixed the problem. Now he would like to restore the primary to
active status. Which one of the following commands can reactivate the primary adaptive security
appliance and restore it to active status while issued on the primary adaptive security appliance?
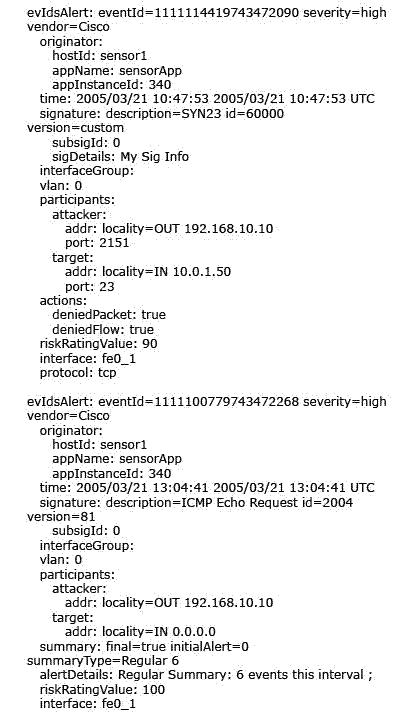
Which three values are used to calculate the risk rating for an event?
Which three values are used to calculate the risk rating for an event? (Choose three.)
How should you create a custom signature that will fire when a series of pre-defined signatures …?
How should you create a custom signature that will fire when a series of pre-defined signatures
occur and you want the Cisco IPS Sensor to generate alerts only for the new custom signature,
not for the individual signatures?
What should be taken into consideration while performing Cisco NAC Appliance design?
What should be taken into consideration while performing Cisco NAC Appliance design? Select all
that apply.
Which of the following statements best describes how IP logging should be used?
Which of the following statements best describes how IP logging should be used?